Reference no: EM131658367
Advanced Network Security Assignment
Question 1 - Firewalls
Objective: be able to design packet filtering firewall rules and identify advantages/disadvantages of such firewalls
An educational institute has a single router, referred to as the gatewayR, connecting its internal network to the Internet. The institute has the public address range 142.66.0.0/16 and the gateway router has address 142.66.123.1 on its external interface (referred to as interface ifout). The internal network consists of three subnets:
- A DMZ, which is attached to interface ifdmz of the gateway router and uses address range 142.66.13.0/24.
- A small network, referred to as shared, with interface ifin of the gateway router connected to two other routers, referred to as staffR, and studentR. This network has no hosts attached (only three routers) and uses network address 10.4.0.0/16.
- A staff subnet, which is for use by staff members only, that is attached to the staffR router and uses network address 10.4.10.0/24.
- A student subnet, which is for use by students only, that is attached to the studentR router and uses network address 10.4.20.0/24.
In summary, there are three routers in the network: the gateway router, and routers for the staff and student subnets. There are four subnets: DMZ, shared, staff, and student. There are three servers in the DMZ that all can accept requests from the Internet:
1. A web server supporting HTTP and HTTPS (IP address is 142.66.13.10)
2. A secure shell server using SSH (IP address is 142.66.13.20), and
3. A SMTP email server (IP address is 142.66.13.30).
Members of the staff and student subnets can access the web server; members of the staff subnet only can access the email server but using IMAP; and internal members (both staff and students) cannot access the SSH server.
The gateway router also runs a stateful packet filtering firewall and performs port address translation. In addition to the DMZ setup as described above, security requirements for the educational institute are:
- External Internet users cannot access any internal computers (except in DMZ and as stated in other requirements).
- Staff and students can access websites in the Internet.
- The SSH server in the DMZ can only be accessed by external Internet users from subnets: 31.13.75.0/24 and 23.63.9.0/24.
Considering the above information, answer the following questions:
(a) Draw a diagram illustrating the network. Although there may be many computers in the staff and student subnets, for simplicity you only have to draw three computers in the staff subnet and three computers in the student subnet. Label all computers and router interfaces with IP addresses.
(b) Specify the firewall rules using the format as in the table below. You may add/remove rows as needed. After the table, add an explanation of the rules (why you design the firewall rules the way you did).
(c) When using iptables as firewall software, you can change the default policy using the -P option. Explain the two common default policies, and explain the tradeoffs between the policies.
Question 2 - WiFi Security
Objective: Understanding important challenges with securing WiFi networks
Defense-in-depth is an important principle in network security. Consider you are advising a company in deploying a WiFi network. You advise them to use all of the following security mechanisms to provide defense-in-depth. For each mechanism, give a brief description of the mechanism and how it works, explain the main advantage of the mechanism, and explain the main disadvantage of the mechanism.
(a) WPA
(b) Using antennas, transmit power and AP positioning to control radio range
(c) RADIUS (or similar) authentication
(d) Manual detection of rogue APs
Question 3 - Access Control
Objective: Understand how Linux passwords and access control operates
For this question you must use virtnet (as used in the workshops) to study Linux access control and passwords. This assumes you have already setup and are familiar with virtnet. See Moodle and workshop instructions for information on setting up and using virtnet, and using Linux access control comments.
Your task is to:
1. Create topology 1 in virtnet
2. Create five new users using realistic usernames. Set the passwords to be different except for two users (that is, two users have the same password, the other users have different passwords), however do not use passwords that you use on other systems.
3. View the password information stored for the new users in /etc/passwd and /etc/shadow. Understand the information stored.
4. Create three new groups named student, teacher, and coord (short for coordinators). Allocate the users to groups as follows:
- User 1: primary group student
- User 2: primary group student
- User 3: primary group teacher
- User 4: primary group coord, also in teacher
- User 5: primary group is their own (i.e. not in student, teacher or coord).
5. Create the following files and directories for each user. Unless specified, the files/directories can be any name and can contain any content:
- Both students (User 1 and 2) have directories security, personal and shared in their home directory. All teachers have read-only access to each students security directory (and files within). All users have read/write access to each students shared directory. Only the user can access their personal directory.
- The coordinator (User 4) has directory security, which has two subdirectories: content and marking. content is read-only by all teachers. marking is only accessible by the user.
- The remaining teacher (User 3) has directories security and personal. security is editable by teachers and coordinators, while personal is only accessible by the user.
- Each directory mentioned above should have at least 1 file in it (the name and contents of the file doesn't matter).
- Every user (including User 5) has a file in their home directory called schedule.txt. This file is readable by everyone.
- Both students have a file in their home directory called submit.bash and it is executable by the user and coordinator.
6. In addition to the access control rules mentioned above, assume:
- Every user has read, write permissions on their own files, and full permissions on their own directories.
- No other user can access the files/directories of other users.
- If permissions are not covered by the above, then assume the defaults.
- If there are conflicts in the above, then assume the most restrictive permission.
- Use only the basic Linux permissions (see example commands below). Do NOT use advanced permissions such as with setfacl or getfacl.
7. Test that the access control works by logging in as each user and checking they can(not) access the specified files/directories.
Answer the following questions after completing the task.
(a) Submit the following files on Moodle:
a. /etc/passwd named as passwd.txt when you submit
b. /etc/shadow as shadow.txt
c. /etc/group as group.txt
d. The output of the following command as files.txt: sudo sh -c 'ls -lR /home > /home/network/files.txt'
(b) Explain where and how password information is stored in Linux. You should mention the files, formats of storing passwords (e.g. what is stored, how is the information created) and any specific algorithms used.
(c) Explain why it is difficult for an administrator to know if two users use the same password.
(d) If a malicious user obtains the file(s) where password information is stored, and users selected long random passwords, then explain why it is difficult for them to find users' actual passwords.
Question 4 - HTTPS and Certificates
Objective: Learn the steps of deploying a secure web server, as well as the limitations/challenges of digital certificates
For this question you must use virtnet (as used in the workshops) to study HTTPS and certificates. This assumes you have already setup and are familiar with virtnet. See Moodle and workshop instructions for information on setting up and using virtnet, deploying the website, and testing the website.
Your task is to:
- Create topology 5 in virtnet
- Deploy the MyUni demo website on the nodes
- Setup the webserver to support HTTPS, including obtaining a certificate certificate.pem. Make sure you use your name or ID in the certificate (e.g. in the email address field) so that it is unique across the class.
- Capture traffic from the web browser on node1 to the web server that includes a HTTPS session. Save the file as https.pcap.
- Test and analyse the HTTPS connection.
Answer the following sub-questions based on above test and analysis.
(a) Submit your certificate certificate.pem and HTTPS traffic capture https.pcap on Moodle.
(b) Explain how the client obtains the certificate of the web server.
(c) Explain how the client verifies the certificate of the web server, and what pre-conditions exist such that the verification is possible.
(d) At the bottom of your certificate there should be a field called "Signature Algorithm", followed by a multi-line random looking hex value. This value is the signature. Explain how the signature is generated. Refer to specific algorithms and information that is used in generating the signature.
(e) In practice, Certificate Authorities must keep their private keys very secure, usually storing them offline in special hardware devices. Explain an attack a malicious user could be perform if they could compromise the CA private key. Use your MyUni website as an example.
Question 5 - Internet Privacy
Objective: Understand the advantages and disadvantages of Internet privacy technologies, including VPNs, and learn about advanced techniques (Tor)
Encryption is commonly used to provide data confidentiality in the Internet: when two hosts communicate, other entities in the path between the two hosts cannot read the data being sent. However encryption on its own does not privacy of who is communicating. Although the other entities cannot read the data, they can determine which two hosts are communicating.
Assume you want to have privacy protection while web browsing. Normally, when your client computer sends a HTTP GET request to a web server, the IP address of both your client computer (C) and the web server (S) are included in the IP header of the packet. Any intermediate node on the path between client and server in the Internet can see the values of C and S, thereby learning who is communicating.
Three common techniques for privacy protection, i.e. hiding both values of C and S from intermediate nodes, in the Internet are:
(a) Web proxies
(b) VPNs
(c) Tor
For each technique, provide the following:
1. An explanation of the technique (you may refer to the diagram)
2. A diagram showing the addresses learnt by a malicious user if the technique is used.
3. A recommendation of who or what this technique is good for. (Consider the advantages of the technique compared to the other techniques, and consider the skills and/or requirements of different users).
4. What a malicious user would need to do to compromise the privacy (i.e. learn both C and S) if the technique was used.
For your diagrams you may use the following simple view of an Internet path where client C is communicating using IPv4 with server S. There are n routers on the path. Assume a malicious user, who wants to know information about who is communicating and when, has access to one of the routers in the path (router Rm), e.g. they can capture packets on that router. Note Rm is not directly attached to the subnets of C or S.
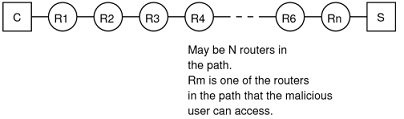
You may use the above diagram (or similar a diagram) to illustrate each of the techniques.
Attachment:- Assignment File.rar