Reference no: EM13669511
Assignment 1: Graph Coverage
For your Assignment 1, complete the following exercises:
1. Answer questions (a)-(d) for the graph defined by the following sets:
N = {1, 2, 3, 4, 5}
N0 = {1}
Nf = {5}
E = {(1,2), (2,3), (1,3), (2,4), (4,1), (3,5)}
a) Draw the graph (Do not use a generation tool. Draw it yourself and scan in or use power point tool or similar one)
b) List test requirements (TR) and test paths for Node Coverage
c) List test requirements (TR) and test paths for Edge Coverage
d) List the test requirements (TR) for Edge-Pair coverage (requirements must be of edge length 2)
2. Answer questions (a)-(c) for the graph defined by the following sets:
N = {1, 2, 3, 4}
N0 = {1}
Nf = {4}
E = {(1,2), (2,3), (1,3), (3,2), (3,4), (1,4)}
Also consider the following (candidate) test paths:
t0 = [1,3,4 ]
t1 = [1, 4]
a) Draw the graph (Do not use a generation tool. Draw it yourself and scan in or use power point tool or similar one)
b) Does the given set of test paths satisfy Edge-Pair Coverage? If not, identify what edge(s) are missing.
c) List test paths that achieve Node Coverage but not Edge Coverage on the graph.
3. Using below definitions for the graph, use Data Flow tool to determine for variable x. Capture the screenshot of at least one execution and paste in the document.
N = {0,1, 2, 3, 4,5,6,7}
N0 = {0}
Nf = {7}
E = {(0,1),(1,2), (2,3), (2,4), (3,5), (4,5), (5,6),(6,5),(6,7),(1,7)}
def(1)=def(3)=use(2)=use(3)=use(6) =use(7)= (x)
def(0)=def(4)=def(6)=use(4)=use(7)=(y)
a) All-def coverage
b) All-use coverage
c) All-du-path coverage
4. Use the following program fragment for questions (a)-(c) below.
a=m; // node 0
y = x; // node 1
if (m > 0)
{
a++; // node 2
}
else
{
a=2*y; // node 3
}
while (x < 5) // node 4
{
y = 5*a; // node 5
x--; // node 6
}
z = a + y; // node 7
(a) Draw a control flow graph for this program fragment (Do not use a generation tool. Draw it yourself and scan in or use power point tool or similar one). Use the node numbers given above.
(b) Which nodes have defs for variable a and which nodes have uses for variable a?
(c) Enumerate all of the du-paths for variable y.
5. For the following questions a-c, consider the method FSM for a (simplified) programmable thermostat. Suppose the variables that define the state and the methods that transition between states are:
partOfDay : {Wake, Sleep}
temp : {Low, Medium, High}
// Initially "Wake" at "Low" temperature
// Effects: Advance to next part of day
public void advance();
// Effects: Make current temp higher, if possible
public void up();
// Effects: Make current temp lower, if possible
public void down();
(a) How many states are there and what are they?
(b) How many edges are there and what are they?
(c) Draw and label the states (with variable values) and transitions (with method names). Notice that all of the methods are total.
(d) A test case is simply a sequence of method calls. Provide a test set that satisfies Edge Coverage on your graph (using state labels).
6. Use activity graph for ATM withdraw funds on page 90 (Fig 2.42) up to Prompt for Transaction and then use the below continuation for transfer selection to answer the (a)-(c) questions.
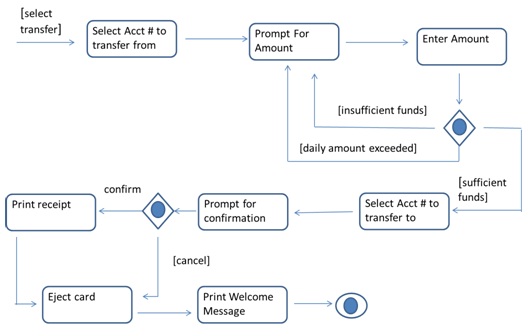
a) Construct a use case to include name, summary, actor, precondition, description, alternatives, and post condition
b) Construct a use case scenario (specific steps through use case)
c) Construct test case for the use case scenario with specific values for purpose, prereq, test data, steps, and expected output.