Reference no: EM131271961
Assignment
This assignment is open notes, open book. Point values are as given; there are 100 total points possible. Please read each question carefully All work is single authorship. Display all references; do not merely quote a reference, but do explain any referenced material in your own words. For full credit, all work must be shown; this includes calculations, derivations, proofs, graphs, as well as your arguments and reasoning. Your methods and reasoning are important.
Problems
1. Consider a three layer protocol in which Layer 3 encapsulates Layer 2 and Layer 2 encapsulates Layer 1. Assume minimalist headers with fixed length packets. Assume the following characteristics of the layers: Layer 1, 6 octet address length, 512 octet payload; Layer 2, 4 octet address length , 256 octet payload; Layer 3, 8 octet address length, 1024 octet payload. Note that in the minimalist header arrangement, no error detection or correction will be used; however, there must be a scheme (that you must devise) to allow a multipacket datagram at each separate layer. You may assume that there is some sort of routing or other address translation protocol that will identify which addresses are to be used. Assume that the data communications channel in use do form a data communications network. (Hint: do recall what is needed for a data communications network as contrasted with an arbitrary graph.)
1.1. For each of the three layers, separately calculated, how many items (nodes) can be addressed? Do not simply show an answer, but ex-plain your reasoning (hint: combinatorics).
1.2. We have discussed functors as a formal, theoretical description be-tween layers of a network. In terms of these three layers, illustrate the functors between the layers, and explain how functors address the di?erences in topology and relevant information content at the di?erent layers
1.3. Assume that the datagram has 5 layer 1 packets. How does this datagram encapsulate in layer 2?
1.4. Taking the above result, or a made-up one of your choosing if you cannot calculate such a result, how does this data from layer 2 en-capsulating layer 1 data then encapsulate in layer 3?
1.5. Assuming that the only information of interest is the payload of layer 1, what is the overall e?ciency of the final encapsulated data stream in layer 3 for the layer 1 datagram described above?
1.6. Assuming that only the information in the starting layer 1 datagram payload is the signal, and the rest of all packets at all layers is noise with respect to this very restricted view of the information content of a channel, what is the e?ective Shannon-Hartley theorem relation between "channel capacity" and "bandwidth" for this specific data-gram?
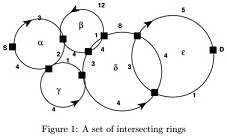
2. Consider a set of intersecting rings as in the following figure. Here, a small square represents a node, including nodes that can transfer packets between rings, and each ring has an arrow that indicates the di-rection of packet flow on that ring. Each ring is labeled by a lower case Greek letter with the first ring labeled.
2.1. Display the adjacency matrix for the network in the figure.
2.2. Which, if any, nodes are equivalent on the network and why? (Hint: recall that equivalence in this context has to do with the number of links to a node as well as the information flow directions to and from a node.)
2.3. Which nodes, if any, represent single points of failure of the network?
2.4. Display the weight matrix for the network.
2.5. Using Dykstra's algorithm, calculate a route from node S to node D on the network as displayed in Fig. 1. Show each step of the algorithm as you develop the route.
|
Compute the maximum throughput t for a pure aloha
: Compute the maximum throughput T for a pure ALOHA and a slotted ALOHA random access system, along with the load L that achieves the maximum in each case.
|
|
Case study - poseidon plc
: Prepare a 2,500 word report responding to the concerns raised by the Board - The Board are particularly concerned that they are able to explain their presence as being beneficial to the local environment whilst they feel that they cannot really den..
|
|
Derive a formula for the optimal power allocation
: Derive a formula for the optimal power allocation on a fading broadcast channel to maximize sum-rate.
|
|
Defining policy and its role in corporate culture
: Defining policy and its role in corporate culture? Write a report on how an organization can achieve ISO 27001 certification.
|
|
Display the weight matrix for the network
: Display the weight matrix for the network. Using Dykstra's algorithm, calculate a route from node S to node D on the network as displayed in Fig. 1. Show each step of the algorithm as you develop the route.
|
|
How do we effectively communicate with adolescents
: How do we effectively communicate WITH adolescents? (in families, in schools, in the media, etc.) - How do we teach adolescents to communicate effectively?
|
|
Differences between formulas and functions
: Discuss the differences between formulas and functions. Pick a function in Excel and discuss how that function is used to calculate results in your worksheets. Review your classmates' posts to make sure that you're not duplicating formulas or func..
|
|
Which of following is not one of the duties of a pharmacist
: Which of the following is not one of the duties of a pharmacist? Today, the pharmacy technician performs many duties formerly completed by the pharmacist. However, it's still not appropriate for the pharmacy technician to
|
|
Word processing program
: In your XXAssign3 folder created in Assignment1, use a word processing program like Word or Writer to create a file called security.
|