Reference no: EM132366259
Algorithms and Complexity
Objectives
To improve your understanding of the time complexity of algorithms and recurrence relations. To develop problem-solving and design skills. To improve written communication skills; in particular the ability to present algorithms clearly, precisely and unambiguously.
Problems
Let's play a game. Or, more precisely, design and analyse some algorithms that might be used in a simple two-dimensional (2D) game.
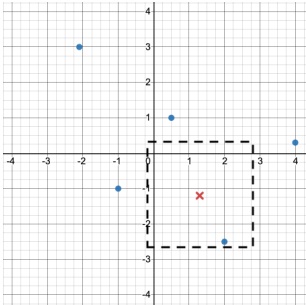
Figure 1: A tiny example game scenario. Enemy (AI-controlled) players are shown in blue. The fixed location of the human player is marked by the red cross.
Consider a game played on an two-dimensional grid, whose Cartesian coordinates range from (-M, M ) . . . (M, M ). Figure 1 depicts a game board for which M = 4.
The game contains a fixed number N of enemy players, who are AI-controlled. Each player (including the human player and each enemy AI) is located at some arbitrary but fixed position (x, y) on the board, for which -M ≤ x ≤ M and -M ≤ y ≤ M .
The human player can perform certain attacks, which damage all enemy players within a certain range of the human player. To avoid the need to calculate with expensive multiplication and square root operations, we will approximate the range by a square situated about the human player.
Specifically, given some fixed bound b, for which 0 ≤ b ≤ M , if the human player is located at position (px, py) then all enemy players that lie within or on the borders of the box whose bottom-left corner is (px - b, py - b) and whose top-right corner is (px + b, py + b) are affected by the attack. Figure 1 depicts an example box for the bound b = 1.5.
1. Implement an Θ(1) function to determine whether an enemy at position ( x, y) is affected by the player's attack, given the player's location (px, py):
function IsAffected((px, py), (x, y), b)
. . .
2. Suppose (for now) that the positions of the enemy players are stored in an unsorted array A[0] . . . A[N - 1].
The following function uses the divide and conquer approach to mark all enemy players affected by a player attack. Marking is implemented by the Mark function whose details are not important. (Note: the division below is integer division, i.e. it rounds down to the nearest integer.)
function MarkAffected((px, py), A, b)
MarkAffectedDC((px, py), A, 0, N - 1, b)
function MarkAffectedDC((px, py), A, lo, hi , b) d assume lo ≤ hi
if lo = hi then
if IsAffected((px, py), A[lo], b) then
Mark(A[lo])
else
mid ← lo + (hi - lo)/2 MarkAffectedDC((px, py), A, lo, mid , b) MarkAffectedDC((px, py), A, mid + 1, hi , b)
Explain the purpose of the outermost "if /else" test. In particular, suppose we removed the line "if lo = hi " and the "else" line. In no more than a paragraph explain how this would affect the algorithm.
3. Consider the following recurrence relations. Which one best describes the worst-base complexity of the MarkAffectedDC function, whose input size is n = hi - lo + 1 and whose basic operations are calling IsAffected and Mark? Justify your answer in no more than a paragraph of text.
T (1) = 1
T (n) = 2T (n/2)
T (1) = 2
T (n) = 2T (n/2) + 2
T (1) = 0
T (n) = 2T (n/2)
T (1) = 2
T (n) = 2T (n/2)
4. Use telescoping (aka back substitution) to derive a closed form for your chosen recurrence relation and thereby prove that the worst case complexity of the MarkAffectedDC algorithm is in Θ(n).
5. Can we do better than this? Recall that the human player is at some fixed location (px, py). Your task is to work out how you would sort the array A so that those enemy AIs that need to be marked can be identified in log(N ) time.
Specifically, complete the following comparison function that would be used while sorting the array A. Here, (x1, y1) and (x2, y2) are two points from the array A. The function should return true if it considers the first point to be less than or equal to the second, and should return false otherwise. Your function can use the player's coordinate (px, py) as global variables, i.e. you are allowed to refer to px and py in your function.
function LessOrEqualTo((x1, y1), (x2, y2))
. . .
6. Now, supposing the array has been sorted using your comparison function, implement an algorithm whose worst case complexity is in Θ(log(N )) that determines which array elements should be marked. Your function should take the bound b as an argument, and may also take the player's coorinates (px, py).
7. How many elements will need to be marked in the worst case and what, therefore, would be the worst-case complexity of an algorithm that, given an array A sorted according to your comparison function, implemented the behaviour of MarkAffected above? Express your answer in Big-Theta notation.
8. The worst case is quite pessimistic. On average, we might expect that enemy AIs are uniformly distributed throughout the game board.
Let d be the expected number of enemy AIs contained in or on the borders of a box of bound b (i.e. whose width and height are each 2b) on the board. For simplicity, we limit our attention to boxes that are contained entirely within the game baord.
Consider an algorithm that, given an array A sorted according to your comparison function, imple- mented the behaviour of MarkAffected above by first using your Θ(log(N )) function to determine the elements that need to be marked (of which we expect there to be d), and then marking those d elements. We might characterise its expected complexity as:
log(N ) + d
Derive a formula for d in terms of b, M and N .
9. As a point of comparison, what is the expected complexity of the divide-and-conquer algorithm above in this average case, expressed in Big-Theta notation? Justify your answer in no more than a paragraph of text.
10. Now compare the best case complexity of the divide-and-conquer algorithm and the one that uses a pre-sorted array A described above. Express the best-case complexity of each in Big- Theta notation as a function of N . Justify both in no more than a paragraph of text.
11. Suppose now that the enemy AIs can send each other messages. However, two AIs, whose positions are (x1, y1) and (x2, y2) respectively, can directly communicate only if the line (x1, y1) - (x2, y2) that connects them does not pass through the rectangle (including its borders) surrounding the human player whose bottom left corner is (px -b, py -b) and whose top-right corner is (px + b, py + b), where (px, py) is the human player's position.
Implement a function that determines whether two enemy AIs can directly communicate. Include a brief description (no more than a single paragraph) of how your function works, i.e. the rationale behind its design. function CanDirectlyCommunicate((x1, y1), (x2, y2), (px, py), b)
. . .
12. Imagine that your CanDirectlyCommunicate function has been used to construct a graph whose nodes are the enemy AIs, such that there exists an edge between node n1 and n2 if and only if those two AIs can directly communicate. This graph is stored as an adjacency matrix M .
Here the nodes ni are simply the indices of enemy AIs in the array A, so each of them is simply an integer in the range 0 ≤ ni ≤ N - 1. Therefore the adjacency matrix M is simply a two-dimensional array, M [0][0] . . . M [N - 1][N - 1].
Implement an O(N 2) algorithm that, given two enemy AIs n1 and n2 determines whether there ex- ists a path by which they might communicate via other enemy AIs. If a path exists, your algorithm should return the shortest path by which communication is possible. Otherwise, your algorithm should return the empty path. Your algorithm also takes as its input the adjacency matrix repre- sentation of the graph described above.
You should represent a path as a linked list of enemy AI indices ni. The empty path is therefore the empty linked list without any nodes.