Reference no: EM132900480
Assessment Brief
Build and Configure Small Network
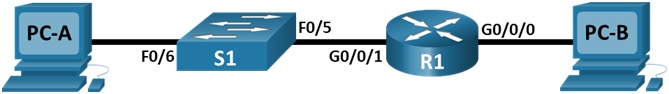
Topology
Assessment Objectives
Part 1: Develop an IP Addressing Scheme
Part 2: Configure Device IP address and Security Settings
Part 3: Test and Verify IPv4 and IPv6 End-to-End Connectivity
Scenario
You are required to build and configure the devices in a small network as shown in the above topology in Packet Tracer. You must configure a router, switch and PCs to support both IPv4 and IPv6 connectivity. You will configure security, including SSH, on the router. In addition, you will test and document the network using common CLI commands.
Requirements
Part 1: Develop an IP Addressing Scheme
a. Please refer to Moodle IP addressing scheme file for your allocated IPv4network address. Use variable-length subnet masking (VLSM) for your design to minimise wastage.You will subnet the provided IPv4 network address to provide IP addresses to the two subnets that will support the required number of hosts.Subnet A has 31 hosts and subnet B has 63 hosts. PC-A is in subnet A and PC-B is in subnet B. No subnet calculators may be used. All workout must be shown(without in-depth discussion on the subnetting method, there will be no mark awarded to this task). Results should be recorded in the IP Addressing table below
|
Specification
|
Subnet A
|
Subnet B
|
|
Subnet address
|
blank
|
blank
|
|
Number of usable hosts per subnet
|
blank
|
blank
|
|
Broadcast address
|
blank
|
blank
|
b. Record your subnet assignment in the table below
1) Assign the first IPv4 address of the relevant subnet to each router interface
2) Assign the last IPv4 address of the relevant subnet to each PC NIC
3) Assign the second IPv4 address of the relevant subnet to S1
|
Device
|
IP address
|
Subnet Mask
|
Gateway
|
|
PC-A
|
Blank
|
blank
|
blank
|
|
R1-G0/0/0
|
Blank
|
blank
|
N/A
|
|
R1-G0/0/1
|
Blank
|
blank
|
N/A
|
|
S1
|
Blank
|
blank
|
blank
|
|
PC-B
|
Blank
|
blank
|
blank
|
c. Assign the first IP address of 2001:db8:acad:0001::/64 network to R1's G0/0/1 interface, second address to S1 and third address to PCA. Assign the first IP address of 2001:db8:acad:0002::/64 network to R1's G0/0/0 interface and second address to PCB. Record the IPv6 addresses information for each device in the table
Note: Use FE80::1 as the link-local address on both router interfaces.
|
Device
|
IPv6 address
|
Prefix Length
|
Gateway
|
|
R1-G0/0/0
|
Blank
|
blank
|
N/A
|
|
R1-G0/0/1
|
Blank
|
blank
|
N/A
|
|
S1
|
Blank
|
blank
|
blank
|
Part 2: Configure Device IP Address and Security Settings
Note: Marks will only be awarded if a screenshot evidence of the configuration is provided
Step 1: Configure intermediary devices
• Set the router hostname as R1
• Set switch hostname as S1
• Set an encrypted privileges EXEC password for all intermediary devices: ccnaenpass
• Secure the console access to all intermediary devices with the password: ccnaconpass
• Set the minimum length for passwords to be 10 characters
• Create an administrative user in the local database and set the username and password as:
Username: admin
Password: admin1pass
• Configure an MOTD banner for all intermediary devices with the message: No Unauthorised Access!
• Encrypt all the used passwords on all intermediary devices.
• Disable IP domain lookup on all intermediary devices.
• Enable synchronous logging on all intermediary devices to avoid interruptions during configuration tasks.
• Configure router's interfaces
o Set description for the interface
o Assign IPv4 and IPv6 unicast and link-local addresses
• Configure switch's management (SVI) interface
o Set description for the interface
o Assign IPv4 and IPv6 unicast and link-local addresses
Step 2:Verify intermediary devices configuration.
Use the appropriate commands on the intermediary devices to provide evidence for your configuration. Screenshots should be clearly labelled showing the relevant configuration.
Step 3: Configure host computers.
Configure host computers with IPv4 and IPv6 addresses from their relevant subnets.
Step 4:Verify host computers configuration
Use the appropriate commands on the host computers to provide evidence for your configuration. Screenshots should be clearly labelled showing the relevant configuration.
Part 3: Test and Verify End-to-End Connectivity
Step 1: Use the ping command to test IPv4 and IPv6 connectivity between all network devices. A clearly labelled screenshot with theresult of the ping command for each test should also be provided.
Use the following table to methodically verify connectivity with each network device. Take corrective action to establish connectivity if a test fails:
|
From
|
To
|
IP Address
|
Ping Results
|
|
PC-A
|
R1 G0/0/0
|
IPv4
|
Blank
|
|
PC-A
|
R1 G0/0/0
|
IPv6
|
Blank
|
|
PC-A
|
R1 G0/0/1
|
IPv4
|
Blank
|
|
PC-A
|
R1 G0/0/1
|
IPv6
|
Blank
|
|
PC-A
|
S1 VLAN 1
|
IPv4
|
Blank
|
|
PC-A
|
S1 VLAN 1
|
IPv6
|
Blank
|
|
PC-A
|
PC-B
|
IPv4
|
Blank
|
|
PC-A
|
PC-B
|
IPv6
|
Blank
|
|
PC-B
|
R1 G0/0/0
|
IPv4
|
Blank
|
|
PC-B
|
R1 G0/0/0
|
IPv6
|
Blank
|
|
PC-B
|
R1 G0/0/1
|
IPv4
|
Blank
|
|
PC-B
|
R1 G0/0/1
|
IPv6
|
Blank
|
|
PC-B
|
S1 VLAN1
|
IPv4
|
Blank
|
|
PC-B
|
S1 VLAN1
|
IPv6
|
Blank
|
Step 2: Enter the appropriate CLI command needed to display the following on R1. A copy of the output of the command on R1 should also be included
|
Command Description
|
Command
|
|
Display a summary of important information about the IPv4 interfaces on R1.
|
Blank
|
|
Display the IPv4 routing table.
|
Blank
|
|
Display the Layer 2 to Layer 3 mapping of addresses on R1.
|
blank
|
|
Display detailed IPv4 information about interface G0/0/0 on R1.
|
blank
|
|
Display the IPv6 routing table.
|
blank
|
|
Display a summary of IPv6 interface addresses and status.
|
blank
|
|
Save the current configuration so it will be used the next time the router is started.
|
blank
|
Attachment:- Configure Small Network.rar