Reference no: EM131259907
Cryptography
Assignment
Overview
In this assignment you will develop an event based onetime password (OTP) system. The system consists of the following components:
1. A soft OTP token UI which consists of a push button and a display control. Clicking on the button will generate and display the onetime password.
2. A test UI which will prompt the user to provide the OTP, show access granted message only if the right OTP is entered.
You will need to do the following:
1. Develop, build and test the UI components.
2. Perform Collision Resistance analysis on both algorithms.
Feedback One-Time Password Algorithm (FOTP):
Hash Feedback One-Time Password Algorithm described in the following chart. Secret key is used as the initialization vector. The first OTP is generated by hashing this vector. The second OTP is generated by hashing the hash generated by the first the 1st OTP, and so on. The OTP is calculated by truncating the hash into a six digit value.
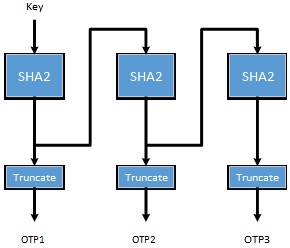
You can set Key = 909670FF00FF00012.
Collision Resistance
This property describes the probability of generating the same OTP over a period of time. A good OTP generation algorithm should demonstrate strong collision resistance. Two metrics are calculated in N number of OTPs:
CR1: the number of similar OTPs in N.
CR2: the number of similar two consecutive OTPs in N.
You will need to submit the following:
1. Complete source code and screen captures of the running program.
2. A study of the collision property. Generate 1,000,000 OTPs using your application. Show a graph describing how the collision properties evolve as the number of OTPs increases.
|
Distinguish between customer service goals and objectives
: Distinguish between customer service goals and objectives. How do characteristics such as substitutability and product life cycle stage influence the development ofcustomer service goals and objectives?
|
|
Competitive analysis of product
: Consider yourself in a leather industry. How would you do competitive analysis of your product (leather jackets) with the help of Porter's Forces Model?
|
|
Discuss how human factors influence the effectiveness
: are the major cybersecurity issues related to the above topic? What policy controls would you recommend to help manage the above topic? Discuss how Human Factors influence the effectiveness of these recommended policy controls.
|
|
What is the total amount of interest expense
: Assume that a machine was purchased for $50,700. Cash of $21,700 was paid, and a four-year, 14% note payable was signed for the balance. What is the total amount of interest expense that will be reported over the life of the note?
|
|
Develop an event based onetime password system
: Develop an event based onetime password (OTP) system - A study of the collision property. Generate 1,000,000 OTPs using your application. Show a graph describing how the collision properties evolve as the number of OTPs increases.
|
|
What is the leader''s function in this conceptualization
: What is meant by "substitutes for," and "neutralizers of," leadership? Give some subordinate, task, and organizational examples of these substitutes and neutralizers.
|
|
Should us government play in health coverage for americans
: What role, if any, should the U.S. Government play in health care coverage for Americans? Should the government's role in terms of health insurance be different for those with jobs and for those without jobs?
|
|
Does the detective have to turn the case over to the fbi
: Better yet, how does the detective get jurisdiction over the criminal even if he or she can be located? Or does the detective have to turn the case over to the FBI? Scotland Yard? Interpol? What if what you want to prosecute is not against the law..
|
|
Describe what is meant by an authentic leader
: What is the GLOBE project? What cultural dimensions have been identified by the GLOBE researchers? What findings have been found by this GLOBE research effort in terms of the six major leadership dimensions found in various cultures?
|