Reference no: EM132780853
Activity - Network Design Practical
1. Design a small-business LAN Logical Topology
2. Design a small-business Subnetting Scheme
Activity Outcomes: After completing this activity you should be able to
1. Demonstrate course knowledge to design an small-business LAN
Task 1. Design a Logical Topology with the following constraints:
Material Constraints:
• 2x 24-Port Layer 3 Network Switches
• lx Edge Router (connected out to the local LAN, the external RV21 5W LAN, and the WAN - 3 total connections)
• 2x Wireless Access Points
• lx Cisco RV215W (connected to the edge router to allow LAN communication from another building)
• 30 total network devices (these will determine your total subnets/VLANs and subnet scopes):
- 10 VolP phones
- 4 Executive computers
- 2 Administration computers
- 2 Finance computers
- 3 Printers
- 2 IT computers
- 2 Servers
- 5 network transport devices (listed above)
- The Cisco RV215W
Logical Topology:
1. Use the image-editing tool of choice (a picture of pen-and-paper is fine)
2. Create a logical topology of the network you described above
3. Remember: Physical location is irrelevant in a logical topology, only how our devices are connected (VLAN's, Subnets, connection types, etc.) need to be included.
4. You need to include the following in your topology:
All device IP addresses
All port numbers used (most important on switches and routers)
Give all devices appropriate host names (excluding the VolP phones)
An example of a partially completed Logical Topology with the given constraints.
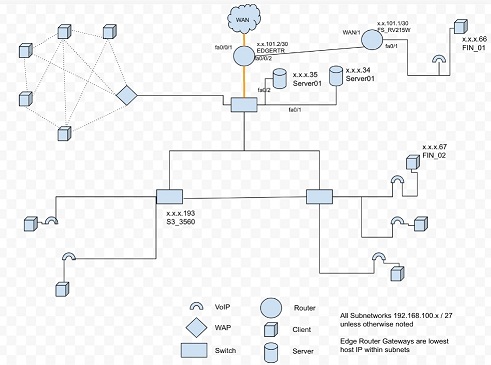
Task 2. Create a subnet scheme based upon the above functions and devices per function.
**(Use a Private Class C: 192.168.100.x)**
1. Document your subnet scheme as a list containing the Department/Function name, Net ID, host range, and Broadcast ID for each.
2. Don't forget to allocate an additional 1192.168.x.x/30 for your router-to-router (Edge Router to RV215W) connection and identify that in your list.
This subnet does not need to fall within the listed IP constraint.