Reference no: EM132284901 , Length: word count:1500
PART-1
Q1. (Privacy-Preserving Computation)
Suppose there are 9 voters to vote for YES or NO to give their opinions.
Design a secure voting prototype as shown in Figure-Q1 using Paillier cryptosystem where the votes must be encrypted from Voting Booth before sending them to the Voting Server.
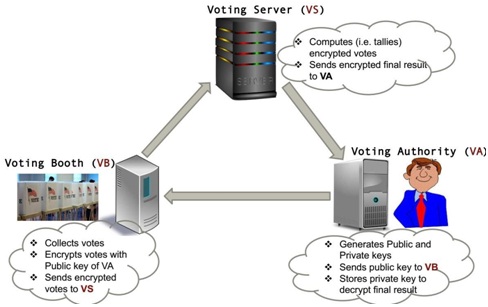
Figure-Q1: Secure voting system
Assume, five voters will vote for YES and four voters will vote for NO. The Voting Authority should find five YESs and four NOs after counting the votes. The Voting Authority chooses p=37, q=73 and select g=9868. The private numbers chosen by 9 voters and their votes are as follows:
|
Voter
No.
|
Voter's Private Number, r
|
Vote
|
Voting message,
m
|
|
1
|
20
|
YES
|
00010000 = 16
|
|
2
|
21
|
YES
|
00010000 = 16
|
|
3
|
22
|
YES
|
00010000 = 16
|
|
4
|
23
|
YES
|
00010000 = 16
|
|
5
|
24
|
YES
|
00010000 = 16
|
|
6
|
25
|
NO
|
00000001 = 1
|
|
7
|
26
|
NO
|
00000001 = 1
|
|
8
|
27
|
NO
|
00000001 = 1
|
|
9
|
28
|
NO
|
00000001 = 1
|
Show the encryption, homomorphic computations and decryption processes. [Hints: Refer to the lecture-5 Secure e-voting. You need to represent the total number of votes by 8-bit string. The first 4 (four) bits should represent the votes for YES and the rests for NO. When adding a vote for YES, the system adds 00010000, which is 16 in integer. Similarly, the system adds 00000001 when voting for NO, which is 1 in the integer form.]
Q2.
Suppose Bob and Alice, two business partners, use their smart phones to communicate with each other regarding their business decisions. Hence, their messages are very sensitive and require to be authenticated. Otherwise, an attacker, say one of their business rivals, may perform phone number porting fraud attack. In this attack, the attacker may use another SIM card to port Alice or Bob's phone number for pretending as Alice or Bob, respectively. Therefore, BoB and Alice uses digital signature scheme in their smart phone to sign messages for ensuring authenticity. The working procedure of the digital signature is illustrated in FigureQ2.
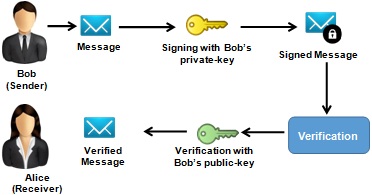
Answer Q2.1, Q2.2 and Q2.3 using the scenario mentioned above.
Q2.1
Suppose Bob (the sender) wants to send a message m=654321 to Alice (the receiver). However, before sending the message he would like sign the message. When Alice receives the signed message, she would like to verify that the message is indeed from Bob. To facilitate signing and verification Bob generates public and private keys using RSA encryption algorithm and sends the public key to Alice. Bob uses parameter p = 9973 and q = 7541, and chooses a suitable public key parameter
e=7321. How would Bob sign message m=654321? How would Alice verify the signed message from Bob?
[Hints: Refer to the lecture-6 and tutorial-6. You do not need to generate hash of the message m.]
Q2.2
Suppose Bob (the sender) wants to send a message m=9876 to Alice (the receiver). However, before sending the message he would like sign the message. When Alice receives the signed message, she would like to verify that the message is indeed from Bob. To facilitate signing and verification Bob generates public and private keys using ElGamal encryption algorithm and sends the public key to Alice. Bob chooses p=8369, g=3031, x=61. How would Bob sign message m=9876? How would Alice verify the signed message from Bob?
Q2.3
Suppose Bob (the sender) wants to send a large text message M to Alice (the receiver). You should download the text message file "Message.txt" from the CANVAS. The text message M is as follows:
The invention of computers in the 20th century revolutionized cryptology. IBM Corporation created a code, Data Encryption Standard (DES) that has not been broken to this day. Thousands of complex codes and ciphers have been programmed into computers so that computers can algorithmically unscramble secret messages and encrypted files.
Before sending the message, Bob generates a hash h(M) of the text message M using MD5 hash algorithm, and converts h(M) into integer message m. Then, he signs the m and sends it to Alice. When Alice receives the signed message, she would like to verify that the message is indeed from Bob. To facilitate signing and verification Bob generates public and private keys using RSA encryption algorithm and sends the public key to Alice. Bob uses the following parameters:
p = 330620674058481288123238031776544995151
q = 273416090781657641961913344431645866621
Bob chooses a suitable public key parameter e=37. How would Bob sign message M? How would Alice verify the signed message from Bob?
Q2.4
Suppose, Bob (the sender) wants to send a message to Alice. Before sending the message, Bob generates a digital signature. Assume that Bob and Alice use both of the public-key cryptography system and hash function when computing digital signatures. Say, the hash function used to compute and verify signatures is insecure, but the public-key cryptography system is secure. Show that Trudy can forge signatures.
Q3 (BlockChain Technology)
Write a well-organized report on how the blockchain technology can impact Smart Industry systems. Please consider the followings in your report sequentially:
a) Explain a motivating scenario of a smart industry where the blockchain can be applied.
b) Explain your understanding with necessary diagrams on how the specified
smart industry can be designed using blockchain.
c) Discuss some popular consensus mechanisms for blockchain. Among the popular consensus mechanisms, which one can be applied in your specified blockchain based smart industry and why? Justify your answer.
d) Explain how the integrity and traceability of smart industry data are obtained using blockchain in your specified scenario.
e) What are the advantages and disadvantages of using blockchain technology in your specified smart industry?
Q4 (Authentication Protocol)
The following mutual authentication protocol is proposed based on a symmetric-key cryptography algorithm. We assume that the cryptography algorithm that is used here is secure. Given that the following protocol does not provide mutual authentication. Give two different attack scenarios where Trudy can convince Bob that she is Alice. Briefly explain each attack scenario performed by Trudy with proper diagram which on the protocol.

[Hints: You need to show two attack scenarios performed by Trudy with proper diagram on the protocol. Additionally, provide brief explanation of attacks to justify
your answer. Refer to attack scenarios on mutual authentication protocols that were discussed during the Lecture-7 and Tutorial-7.]
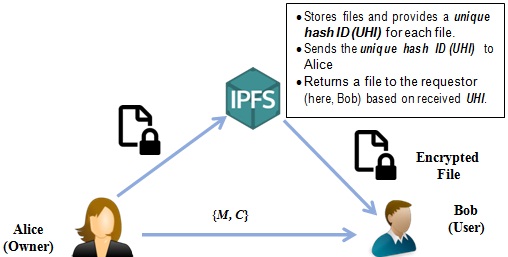
Q5 (OpenSSL and IPFS)
Assume that the School of Science of RMIT University is planning to use IPFS-based repository of sensitive files for sharing among staffs. An owner of a particular file, say Alice wants to share the file to her supervisor, say Bob. Therefore, Alice encrypts the file with Alice and Bob's shared AES secret key (KAB) using OpenSSL, uploads the encrypted file in the IPFS-based repository, and receives a Unique Hash Identifier (UHI). Next, Alice encrypts KAB and UHI with Bob's RSA public key using OpenSSL and gets ciphertext C. Further, Alice generates a message digest M using OpenSSL with her RSA private key for the ciphertext C. Finally, Alice sends {M, C} to Bob through email.
Upon receiving them, Bob verifies the message digest M using OpenSSL with Alice's RSA public-key. If the verification fails, Bob discards further steps and informs Alice that the verification has been failed. If the verification is successful, Bob decrypts C using OpenSSL with his RSA private-key. If the decryption is successful, Bob retrieves the shared AES secret key (KAB) and unique hash identifier (UHI) for the file.
Bob downloads the file from IPFS-based repository with the file's UHI. Bob uses IPFS commands to download the file. Upon receiving the file from IPFS network, Bob decrypts the encrypted AES secret key. Finally, Bob decrypts the download file from IPFS network using the shared AES secret key (KAB). The scenario is illustrated in the Figure-Q5 below. Show the required OpenSSL and IPFS commands sequentially for each step stated above. Please provide screenshot of the outcome for each command.
Attachment:- SECURITY IN COMPUTING AND IT.rar