Reference no: EM133528735
Network Security
Overview
The learning objective of this assignment is for you to gain a first-hand experience on network attacks (i.e., TCP and DNS attacks) and get a deeper understanding on how to launch these attacks in practice. All tasks in this assignment can be done on the virtual machine
TCP Attacks - Using Scapy
The Transmission Control Protocol (TCP) is a core protocol of the Internet protocol suite. It sits on top of the IP layer, and provides a reliable and ordered communication channel between applications running on networked computers. TCP is in a layer called Transport layer, which provides host-to-host communication services for applications. To achieve such reliable and ordered communication, TCP requires both ends of a communication to maintain a connection. Unfortunately, when TCP was developed, no security mechanism was built into this protocol, making it possible for attackers to eavesdrop on connections, break connections or hijack connections. In this section, you are required to perform these attacks using Scapy-a packet manipulation tool for computer networks written in Python.
Task 1: TCP Reset Attacks
In the stream of packets of a TCP connection, each packet contains a TCP header. In the header, there is a bit known as the "reset" (RST) flag. In most packets, this bit is set to 0 and has no effect; however, if this bit is set to 1, it indicates that the receiver should immediately stop using the TCP connection. That means it should not send back any more packets using the connection's identifying numbers, called ports, and discard any further packets with headers belonging to that connection. A TCP reset basically kills a TCP connection instantly.
It is possible for a third computer (aka attacker) to monitor the TCP packets on the connection and then send a "forged" packet containing a TCP reset to one or both endpoints. The headers in the forged packet must indicate, falsely, that it came from an endpoint, not the forger. This information includes the endpoint IP addresses and port numbers. Every field in the IP and TCP headers must be set to a convincing forged value for the fake reset to trick the endpoint into closing the TCP connection.
The idea is quite simple: to break up a TCP connection between A and B, the attacker spoofs a TCP RST packet from A to B or from B to A.
Question 1: Connect from Int;ernal-Client; to Internal-Server using SSH (use apt; install ssh if SSH is not installed), the username and password are the same: msf admin. Perform TCP RST attack, from Internal-At;tacker workstation, on SSH service using Scapy (python-based) packet generator. Int;ernal-Client; terminal should show the connection is terminated. Please record and submit a video showing and explaining how you performed the attack. A part of the video must show and explain your Python code. Also submit your Python code separately.
Question 2: Describe two theoretical countermeasures (in the recorded video). You do not have to do any config- uration/implementation for this task.
Task 2: TCP Session Hijacking Attacks
Once a TCP client and server finish the three-way handshake protocol, a connection is established, and we call it a TCP session. From then on, both ends can send data to each other. Since a computer can have multiple concurrent TCP sessions with other computers, when it receives a packet, it needs to know which TCP session the packet belongs to. TCP uses four elements to make that decision, i.e., to uniquely identify a session: (1) source IP address, (2) destination IP address, (3) source port number, and (4) destination port number.
We call these four fields as the signature of a TCP session. As we have already learned, spoofing packets is not difficult. What if we spoof a TCP packet, whose signature matches that of an existing TCP session on the target machine? Will this packet be accepted by the target? Clearly, if the above four elements match with the signature of the session, the receiver cannot tell whether the packet comes from the real sender or an attacker, so it considers the packet as belonging to the session.
However, for the packet to be accepted, one more critical condition needs to be satisfied. It is the TCP sequence number. TCP is a connection-oriented protocol and treats data as a stream, so each octet in the TCP session has a unique sequence number, identifying its position in the stream. The TCP header contains a 32-bit sequence number field, which contains the sequence number of the first octet in the payload. When the receiver gets a TCP packet, it places the TCP data (payload) in a buffer; where exactly the payload is placed inside the buffer depends on the sequence number. This way, even if TCP packets arrive out of order, TCP can always place their data in the buffer using the correct order.
The objective of this task is to hijack an existing TCP connection (session) between client and server by injecting malicious contents into their session.
Question 3: Connect TELNET from Internal-Clienc to Internal-Server, the username and password are the same: msf admin. Write a python code, using Scapy, which can inject packets in the TELNET communica- tion, the goal is to make a directory called "attacker" at the Internal-Server (as seen in the screenshot below). You can use Internal-Attacker workstation to run the python code. Please record and submit a video showing and explaining how you performed the attack. A part of the video must show and explain your Python code. Also submit your Python code separately.
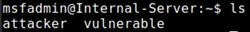
Fig: Directories in Internal - Server
Question 4: Connect TELNET from Int;ernal-Client to Internal-Server. The objective is to get a reverse shell from Internal-Server. Reverse shell is a shell process running on a remote machine, corinecting back to the attacker's machine. We are omitting the details of reverse shell and encourage students to research about it, you can start from here. Write a python code, using Scapy, which can inject packets in TELNET communication and create a reverse shell from Internal-Server to Internal-Attacker (as seen in the screenshot below, in this case the Int;ernal-Server's IP address is 10.10.10.197). Please record and submit a video showing and explaining how you performed the attack. A part of the video must show and explain your Python code. Also submit your Python code separately.
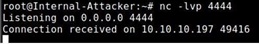
Question 5: Connect SSH from Internal-Cl ienc to Int;ernal-Server, the username and password are same: msf admin. Perform same TCP hijacking attacks as you did for TELNET, i.e. make attacker directory in Int;ernal-Server and create a reverse shell from Internal-Server to Internal-AU acker by hijacking SSH connection. Please record and submit a video showing and explaining how you tried to perform the attack and why it was or was not successful. A part of the video must show and explain your Python code. Also submit your Python code separately.
DNS Attacks - Using Scapy
Domain Name System (DNS) is an essential component of the Internet infrastructure. It serves as the phone book for the Internet, so computers can look up for a "telephone number" (i.e. an IP address) from domain names. Without knowing the IP address, computers will not be able to communicate with one another. Due to its importance, the DNS infrastructure faces frequent attacks. In this section, you will explore the most primary attack on DNS. That is DNS cache poisoning by investigating both Local and Remote DNS cache poisoning attacks.
Due to the large number of computers and networks on the Internet, the domain namespace is organised in a hierarchical tree-like structure. Each node on the tree is called a domain, or sub-domain when referencing to its child node. The following figure depicts a part of the domain hierarchy.
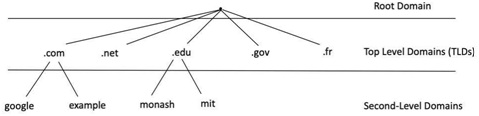
Figure 5: Domain hierarchy
The domain hierarchy tree structure describes how the domain namespace is organised, but that is not exactly how the domain name systems are organised. Domain name systems are organised according to zones. A DNS zone basically groups contiguous domains and sub-domains on the domain tree, and assign the management authority to an entity. Each zone is managed by an authority, while a domain does not indicate any authority information. The following figure depicts an example of the example . com domain.
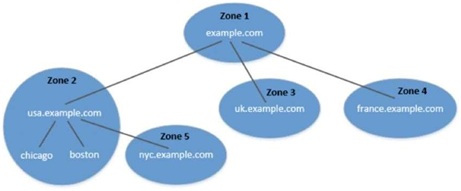
Figure 6: DNS Zones
Assume that example . con in the above figure is an international company, with branches all over the world, so the company's domain is further divided into multiple sub-domains, including usa. example . com, uk. example . com, and france . example . com. Inside US, the usa sub-domain is further divided into chicago, bost;on, and nyc subdomains.
Each DNS zone has at least one authoritative nameserver that publishes information about that zone. The goal of a DNS querv is to eventually ask the DNS server for answers. That is why they are obtaining the answers from other DNS servers.With such arrangement, the root zone for example.com only needs to keep records of who the authority is for each of its subdomains. By doing this, it maintains the independence among the branches in different countries and enable the administrative right of those subdomains, so the branch in each country manages its own DNS information. For a given DNS query, if your local DNS server does not know the answer, itasks other DNS servers on the Internet for answer via hierarchical authority servers. The following example demonstrates a dig (DNS query) for the domain wv. example . net; when sending the query directly to one of the root servers (i.e. a. root-servers . net).
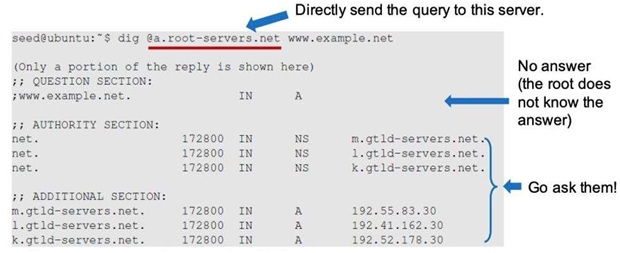
Figure 7: DIG to the root server
There are four types of sections in a DNS response: question section, answer section, outhoN/y section, and additional section. From the above result, we can see that the root server does not know the answer (because the reply does not include an answer section, but it tells several authoritative nameservers for the net zone (the NS records in the authority section), along with their IP address if possible in the additional section). If you continuously dig the domain wv. example . net on one these authoritative nameservers, you will finally end up with the answer section showing the IP address of the machine hosting the website for nun . example . net.
When your local DNS server gets information from other DNS servers, it caches the information, so if the same information is needed, it will not waste time to ask again.
Task 3: Local DNS Attack targeting Authoritative Nameserver
We recalled that a DNS response contains question section, answer section, authority section, and additional section. If we only target the anstrer section, the attack only affects one hostname (as we did in our Week07 lab "DNS Spoofing Attacks"). Real DNS attacks usually target the authority section by providing a fake NS record for the target domain in the authority section. If the fake NS record is cached, when a victim's local DNS server tries to find any IP address in the target domain, it will send a request to the malicious nameserver specified in the fake NS record. Such an attack can affect all the hostnames in the target domain. In this task, you will explore how to target the authoritative server of example . net and replace it with ns1. attacker . com and ns2. attacker . com.
Question 6: Using Internal-Client as victim and Int;ernal-Attacker as the attacker machine, perform a DNS spoofing attack that modifies the authoritative server of example . net to be ns1. at;t;acker . com and ns2. attacker . com. Please record and submit a video showing and explaining how you performed the attack. A part of the video must show and explain your Python code. Also submit your Python code separately.
Hint: If the attack works, you should see a result as in the following figures for which the malicious authoritative servers have taken place.
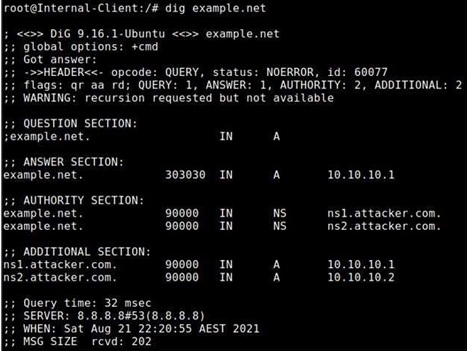
Figure 8: Q6
Question Task 4: Remote DNS Attack targeting Authoritative Server
For this task, the attacker (Internal-Attacker) and DNS server need to be in different LAN. We will move DNS server to Server LAN and configure its IP statically. The GNS3 configuration for this task should look like below:
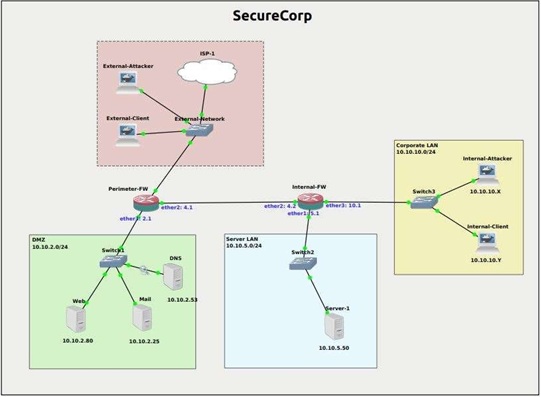
Figure 9: GNS3 for Remote DNS Attacks
Configure static IP for DNS:
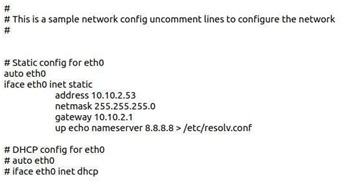
Figure 10: Static IP config for DNS
Now login to Int;ernal-FW (username is ‘admin', no password), and execute the following to disable NAT:
The previous local DNS attacks assume that the attacker and the DNS victim server are on the same LAN so that the attacker can observe the DNS query message and reply with a forged DNS packet. When the attacker and the DNS server are not on the same LAN, the attack becomes harder since the attacker cannot perform ARP poisoning attack and see the DNS query. When the DNS victim server cannot resolve a DNS query, it forwards the DNS query packet to the forwarder DNS server (Google DNS server in our current setup). The DNS query is sent via a UDP packet where the UDP's source port is a 16-bit random number. In addition, the 16-bit transaction ID in the DNS header is also self-created by the DNS victim server. Hence, if the remote attacker wants to forge the DNS response, the forged packet must contain the correct values of these two numbers; otherwise, the reply will not be accepted.
Without being able to sniff the query packet, the remote attacker can only guess these two numbers. The chance is one out of 232 for each guess. If an attacker can send out 1000 spoofed responses, it may take several days to try up 232 time. In contrast, it only takes few seconds to receive the correct packet response from the forwarder Google DNS. Consequently, that real reply will be cached by the local DNS victim server. To make another try, the attacker has to wait for the server to send out another DNS query when its cache times out. Hence, this attacking chance makes the remote DNS attack unrealistic.
The remote DNS attack had become an open problem until Dan Kaminsky came up with a simple trick in 2008. The attack is depicted in the following figure.
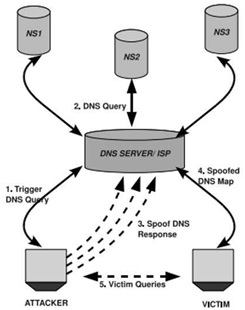
Figure 11: Kaminsky Attack
We choose a domain test .com as our targeted domain name in this task. When a client queries the DNS server for ww. t;est; . com, the attacker (Internal-At;tacker) wants to cause the DNS server to use their DNS server (ns . attacker . com). The following steps with reference to above figure describe the outline of the attack.
1. The attacker queries the DNS server for a non-existing name in test; . con, for example xyzl23. test .com, where xyz123 is a random name.
2. Since the mapping resolution cannot be resolved by the DNS server's cache, the server forwards the query to Google DNS (8.8.8.8) for that name resolution.
3. In the meantime, the attacker floods the DNS server with many spoofed DNS responses, each trying a different transaction ID and source port number (hoping one guess is correct). In that forged response, not only the attacker provides the IP resolution for the hostname xyz123 . test .com, but also provides an authoritative name server for the domain Desc . com.
Even if the response failed, the attacker would go back to Step 1, and try another non-existing random name until the attacker succeeds.
4. Once the attack succeeds, when the client sends a DNS query to the poisoned DNS server for wu . test .com, the nameserver returned by the DNS server will actually be set by the attacker.
To simplify and shorten the attack's simulation time in this task, we suggest you follow the below steps before doing the task.
1. Double check the IP addresses of the server, attacker, and client to ensure the server and the attacker are not in the same LAN (using ifconfig command)
o DNS: 10.10.5.53
• Internal-Attacker: 10.10.10.X
• Internal-Client: 10.10.10.X
2. In the DNS server's terminal, you can type the following command to configure DNS
Then, you should configure the forwarder 8.8.8.8, enable recursion and fix the query source port of
transactionID of the DNS packet when performing remote DNS attacks. You can review the following figure for the correct configuration of DNS server.
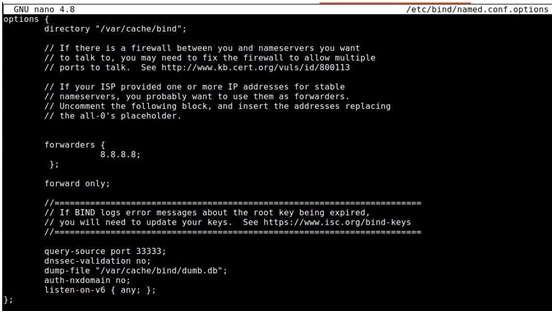
Figure 12: DNS server config file
3. After making the changes in the above step, you should restart your DNS server by using the following command
We provide you the remote dns . py script template on Moodle that helps to perform the Kaminsky attack.
Question 7: You need to complete Step 1 in the remote due . py to create 10000 dummy hostnames. Demonstrate and explain this task as before in your recorded video. Separately submit your Python code.
Question 8: You need to complete Step 2 in the renote dns . py to generate a random DNS query for each dummy hostnames. Demonstrate and explain this task as before in your recorded video. Separately submit your Python code.
Question 9: You need to complete Step 3 in the renote dns . py to flood about 100 random forged response packets. Demonstrate and explain this task as before in your recorded video. Separately submit your Python code. The demo should show that
• Each packet has a randomly generated transaction ID for DNSpkt.
• The malicious DNS server ns. attacker . com is included in the nameserver authority for the domain test; . com when you construct DNSpkt.
• Additional section showing ns. at;t;acker . com has the IP of the attacker 10.10.10.X.
Question 10: Provide further video demonstration evidence to support and verify that you have performed the attack. In the video, you need to demonstrate the following key points:
- Wireshark traffic captured on DNS server on et;h1 shows the transact;ionID in DNS packet sent by DNS server to Google, and the correctly matched transaction ID in the forged packet sent by Int;ernal-At;t;acker to the DNS server. (5 marks for step by step explanation of the attack using Wireshark in the demonstration video)
- Once the poisoning is completed, from Internal-Clienc's terminal use dig command to send a DNS query for the specific subdomain for which the attack was successful (e.g. in below screenshot it's i ssnuy6 . test .com). Do you get the attacker's IP? (5 marks)
- Now from the same terminal send a DNS query for ww . t;est; . con. If the attack was successful, the response should show ns . at;t acker . com in the authority section for the domain t;esc . con. Was your attack successful? Explain in detail why or why not. (hint: you may refer to this paper for further information

Figure 13: Attacker's screen shows poisioning was successful
Acknowledgement
Parts of this assignment and instructions are based on the SEED project (Developing Instructional Laboratory for Computer Security Education).
Attachment:- Network Security.rar