Reference no: EM13753937
Question1: The objective of this question is to
(a) describe the general concepts of TCP/IP protocols and
(b) apply channel capacity theories.
(a) Consider the sending of a UDP segment to its peer entity. The UDP segment consists of 1200 bytes UDP dataplus 8bytes ofheader. Thesegment is encapsulated into anIP datagram that hasan additional 20 bytes of header.TheIPdatagram is in turn encapsulated intoLANframes. EachLAN frame allows apayload of 500 bytes anda header of 26 bytes. Thus,a fragmentation is needed at datalink layer.
(i) Sketch a diagram to show the layering and fragmentation process.
(ii) How many bits, including headers, are delivered to the destination?
(iii) What is the total percentageoverhead of headers?
(b) Comparethewhitenoisepower densitylevels in closed rooms inLondon and Sydney in January, with averagetemperatures of 5oC and24 oC respectively.
(c) Considera communication channel with 10 MHzbandwidth.
(i) If one wishes to transmit at adata rate of150 Mbps, what is the minimum signal- to-noise ratio in dBrequired to accomplish this?
(ii) If thenoise poweris 8 x10-6 Watt, what isits signal power in Watt?
Question2: The objective of this question is to comparedigital encoding and modulation techniques.
(a) Consider thebinarybitsequence,1111000000 00 10 00 0 1.
(i) Draw the wave form for Manchester encoding.
(ii) Draw thewaveform forHDB3encoding.
(iii) What arethe strengths and weaknesses of HDB3 encoding?
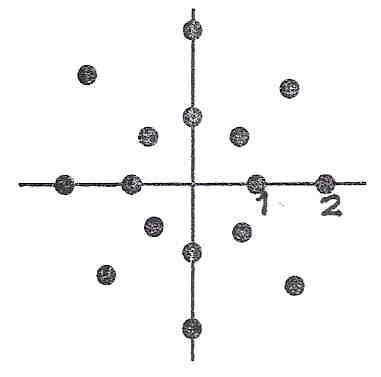
(b) Figure shows the constellation diagram of a modulation technique.
(i) Identify the modulation technique. Explain.
(ii) How manybits can berepresented per signal elementin this modulation technique?
(iii) Given the baud rate of4800bauds, how manybits persecondcan the modem achieve?
(iv) Ingeneral, using QAM, do the same bits always correspond to the sameanalog signal?Explain.
Question3: The objective of this question is to (a) distinguish asynchronous and synchronous transmissions and (b) apply error detection techniques to communications.
(a) Consider the transmission of 16 characters overa10 kbps communication line. Each characterconsistsof 7information bits and oneparitybit.
(i) Calculate the effective data rate of the transmission for Asynchronous transmission usingonestart bit and 1.5 stop bits for eachcharacter.
(ii) Calculate the effective data rate of the transmission for synchronous transmission.
Assume that the data can be accommodated in one data frame with 48 bits overhead.
(b) Consider a transmission system using Cyclic Redundancy Check(CRC) technique with agenerator polynomial 1010111 to generatea Frame Check Sequence(FCS).
(i) If the data to be transmitted is 1 11 1 1010 11, compute the FCS using Modulo 2 arithmetic.
(ii) What is the transmitted frame?
(c) What arethe strengthsofthe CRC technique?
Question 4: The objective of this question is to (a) apply flow/error control techniques to practical problems and (b)describe HDLC protocols.
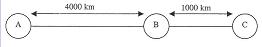
(a) Three nodes, A, B, C are connected by two full duplex links from A to B andfrom Bto C as shown in Figure. The distance AB is 4000 km and BC is 1000 km. Frames generated byA aresent to C throughB. The propagation delay is 5us/km for both links. All data frames are 1000 bits long. ACK frames are separate frames of negligible length. Between A and B, a sliding window protocol with window sizeof 3 is used. Between B and C, a stop-and-wait protocol is used. Assume that thereareno errors in transmission.If the data rate between A and B is 100 kbps, determine the minimum transmitted data raterequired between B and C so that the buffers of B are not flooded.
(b) Consider HDLC protocol.
(i) Apply the bit stuffing rule to the following data string and obtain theoutputstring:
01111001 10111110 11111101 00000010 (leftto right)
(ii) What happens at the receiver if the transmitted sequence is received without errors?
(iii) What happens at the receiver if the transmitted sequence is received with a single bit error in the16th transmitted bit?
|
Amount of net accounts receivable before and after write off
: Norcia Company, which uses the allowance method, began the year with Accounts Receivable of $32,500 and an allowance for uncollectible accounts of $3,200 (credit). What is the amount of net accounts receivable before and after the write-off?
|
|
Gsb management fee
: Suppose venture capital firm GSB partners raised $100 million of committed capital. Each year over the 10-year life of the fund, 2% of this committed capital will be used to pay GSB's management fee.
|
|
Drilling truck account would appear on the balance sheet
: On January 13, 2013, Precision Oil Company purchased a drilling truck for $90,000. Precision expects the truck to last five years or 200,000 miles, with an estimated residual value of $15,000 at the end of that time. Using the amount computed in (3),..
|
|
Complete the systems administration scripting log
: Complete the Systems Administration Scripting Log, As you complete each of the following steps, keep track of what occurs at each point, including what you type, the output given, and any errors experienced.
|
|
Describe the general concepts of tcp/ip protocols
: describe the general concepts of TCP/IP protocols and apply channel capacity theories. Sketch a diagram to show the layering and fragmentation process
|
|
Corporations-partnerships and estates-trusts problem
: In each of the following independent cases, write a memo for the tax research file in preparation for a meeting with Gary. In each memo, explain whether the proposed plan meets his objective of shifting income and avoiding the grantor trust rules. Ga..
|
|
Maintain a minimum balance
: Randy, a student, has $500 to deposit in a new checking account, but Randy knows he will not be able to maintain a minimum balance. He will not use an ATM card, but will write a large number of checks.
|
|
Ending inventory used FIFO-LIFO and average-cost methods
: There are 48 units of the item in the physical inventory on 12/31. the periodic inventory system is used. Determine the dollar value of the ending inventory used the FIFO, LIFO, and average-cost methods.
|
|
Used the aging of accounts receivable method to estimate
: At the end of 2013, Blackhorse Productions, Inc., used the aging of accounts receivable method to estimate that its Allowance for Doubtful Accounts should be $19,650. The account had an unadjusted credit balance of $10,000 at December 31, 2013. The a..
|