Reference no: EM132310695 , Length: word count:1000
Assignment Questions -
Q1. Figure 1 shows a tunnel going through a mountain and two streets parallel to each other-one at each end of the tunnel. Traffic lights are located at each end of the tunnel to control the cross flow of traffic through each intersection. Based on this figure, answer the following questions:
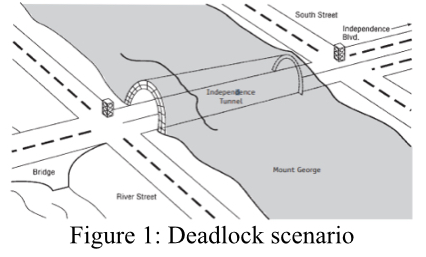
a. How can deadlock occur and under what circumstances?
b. Model the deadlock scenario of figure 1 using the deadlock graph and determine how deadlock can be detected.
c. Research "livelock" and describe it in your own words with example.
d. Describe the difference between "livelock" and "deadlock".
Q2. Research on integration of hardware, operating systems and application software and answer the following:
a. How do computer hardware, OS and application programs work together?
b. Discuss the steps involved with their interactions.
Q3. Reason out why are RAM memory capacities in powers of 2 and why don't hard disk and DVD discs follow the same norm? For instance, 512 KB, 512 MB, 1 MB, 2, 4, 8 MB.
Q4. Describe in your own words the purpose and applications of all user interfaces? Which one you would prefer and why?
Q5. On a disk with 1000 cylinders, number 0 to 999, compute the number of tracks the disk arm must move to satisfy all the requests in the disk queue. Assume the last request serviced was at track 345 and the head is moving toward track 0. The queue in FIFO order contains requests for the following tracks: 123, 847, 692, 475, 105, 376.
Answer the below questions for the following disk scheduling algorithms: FCFS, SSTF, SCAN and LOOK.
a. Draw a diagram for the arm movement.
b. Calculate the total number of tracks and the average number of tracks travelled by the head to satisfy the requests in Q5-a (Details of the calculations is essential).
Q6. Document the following UNIX commands (in clear and concise form):
Each of the above commands must be documented to the extent so that the reader of your report could understand how each command works, including the following points:
- Brief introduction of the function of the command in your own words (in 2-3 sentences).
- The basic syntax of the command, including options. Where appropriate, give a brief description in your own words of at least two options of the command.
- At least two examples of the usage of the command that you have used in lab (provide screen capture).
Q7. As a matter of fact, operating systems are not designed to utmost perfection since at times they suffer from a number of problems. Such problems can be very inconveniencing if one is not familiar with the troubleshooting tools. Hence one should be aware of all these techniques which can resolve the problem so one can continue working without any problems.
What are the common operating system problems? Suggest and provide details of some trouble shooting tools that can be used. List 5 problems and 5 solutions to fix them.
Example:
Invalid boot disk - The invalid boot disk error message mainly appears when there is a problem with one's operating system's boot order. On receiving such a message, make sure that no USB device is plugged in since the BIOS might be configured to boot from external USB devices instead of the local drive. In addition, one can make modifications onto the BIOS configuration so as to modify the devices that should boot first on one's computer.
Fixboot - Fixboot command is used when one wants to create a new boot sector for the operating system. By using this command, one might want to write some new booting sector in a particular partition. When using this command, one might also require using the DISKPART command so as to identify the part or section of the disk one wants to write the new boot sector.
Please Note: Give references and cite the sources that you used for this task.