Reference no: EM131177072
Advanced Network Security Assignment
Question 1 - Protocol Analysis with Wireshark
Objective: gain a good understanding of common Internet protocols as well as using packet capture software (Wireshark).
The file a01-assignment-1-question-1-capture.pcap on Moodle contains packets captured in an exchange between several computers. Use the file to answer the following sub- questions. Some sub-questions refer to only a specific set of packets in the capture.
a) Considering all the packets in the file, draw a message sequence diagram that illustrates the packets. A message sequence diagram uses vertical lines to represent events that happen at a computer over time (time is increasing as the line goes down). Addresses of the computers/software are given at the top of the vertical lines. Horizontal or sloped arrows are used to show messages (packets) being sent between computers. Each arrow should be labelled with the protocol, packet type and important information of the message. An example of a portion of the message sequence diagram for packets 6 and 7 are shown below. You must draw a diagram that shows all packets. Hints:
- The packet times do not need to be shown, and the diagram does not have to be scale.
- The example shows vertical lines representing two computers. You may need another vertical line.
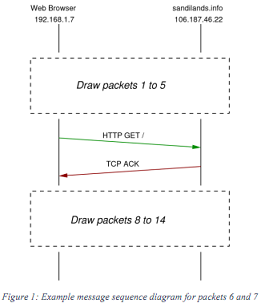
b) For the following sets of packets from the capture, give a short explanation of their purpose/meaning. For example, why were they sent? Which computer sent them? To which computer(s) did they send them to? What is the important information in each packet? What is achieved from the packet exchange?
i. Packets 1 and 2
ii. Packets 3, 4 and 5
iii. Packets 6, 7, 8 and 9
iv. Packets 10 and 11
v. Packets 12, 13 and 14
Question 2 - Application Attacks
Objective: be able to interpret packet captures and identify security weaknesses in web applications.
You have performed a man-in-the-middle attack allowing you to capture packets between two computers. The two computers are named/addressed as follows:
- Web Browser computer: 192.168.1.11
- Web Server computer: 192.168.2.21
The website is a university grading system: students and staff can log in and view grades of courses they are involved with (staff or admin users can also edit grades). Students should not be able to view other students' grades, nor edit grades.
The packets you captured are in file a01-assignment-1-question-2-capture.pcap (on Moodle). They involve a student, with student ID 5012345678, on the web browser computer using the grading website. Unfortunately (for you) the actual login packets were encrypted (using HTTPS) and therefore are not included in the file. Only the packets from after the login are in the file.
By using only the file a01-assignment-1-question-2-capture.pcap and the information in this question, answer the following sub-questions.
a) Describe the actions of the student using the web browser. That is, give the links they clicked on (or typed in), the exact time when they clicked on it (relative to the first packet captured), any parameters or form fields they filled in, and what was displayed on their web browser as a result. You may give your answer as a list, for example:
- At time 0.0 the student clicked on link ... . As a result they were shown a webpage that welcomed them, had a link to "View grades", "Logout" and to several help pages.
- At time ...
b) List all information you know about the student's computer (including addresses and software it uses). For each item of information, explain where you found the item in the capture. For example, one item of information is the IP address:
- The student's computer has IP address 192.168.1.11 as identified in the IP header of each packet.
- The student's computer ...
c) Explain how you could use the captured packets to perform an attack that allows you to login as the student. In your answer, refer to the packets (and information in them) that allow the attack and give a general explanation of how to perform the attack.
d) Regarding the attack in the part (c), check if your favourite web browser allows you to perform the attack. If so, explain what to do with that browser (e.g. "In Mozilla Firefox on Windows 8.1, open the File menu and select ..."). If not, then explain other software/techniques you could use to perform the attack (e.g. "On Windows 8.1 install the software ... and then ..."). Don't forget to include the name of your favourite browser in the answer. Note that you do not have to perform the steps - you only need to find out what they are.
e) Now assume you have also obtained (through other means) the source code of the file view.php in the grades directory on the web server. The file is on Moodle and renamed as a01-assignment-1-question-2-view.php. Assuming your attack from part (c) was successful and you are currently logged in as student 5012345678, explain a different attack you can perform to view the grades of other students. In your answer, explain what you would do to perform the attack and which lines of code in view.php you take advantage of for the attack. Note that you can't use the same attack as part (c); your attack should make use of view.php.
f) Regarding the attack in part (d), explain how view.php could be modified such that the attack would be unsuccessful.
Question 3 - Designing Firewalls
Objective: be able to design packet filtering firewall rules and identify advantages/disadvantages of such firewalls.
An educational institute has a single router, referred to as the gateway router, connecting its internal network to the Internet. The institute has the public address range 138.77.0.0/16 and the gateway router has address 138.77.178.1 on its external interface (referred to as interface ifext). The internal network consists of four subnets:
- A DMZ, which is attached to interface ifdmz of the gateway router and uses address range 138.77.179.0/24.
- A small network, referred to as shared, with interface ifint of the gateway router connected to a second router, referred to as the internal router. This network has no hosts attached (only two routers) and uses network address 10.2.0.0/16.
- A staff subnet, which is for use by staff members only, that is attached to the internal router and uses network address 10.2.1.0/24.
- A student subnet, which is for use by students only, that is attached to the internal router and uses network address 10.2.2.0/24.
In summary, there are two routers in the network: the gateway router is attached to three subnets (external, DMZ and shared); and the internal router is also attached to three subnets (shared, staff and students).
There are three servers in the DMZ that all can accept requests from the Internet: a web server supporting HTTP and HTTPS, a secure shell server using SSH, and a SMTP email server. Internal staff and students can also access the web and secure shell servers; they can access the email server but using IMAP.
The gateway router also runs a stateful packet filtering firewall and performs port address translation. In addition to the DMZ setup as described above, security requirements for the educational institute are:
1. External Internet users cannot access any internal computers (except in DMZ).
2. Both staff members and students can access websites in the Internet.
3. Staff, students and others may have accounts on the SSH server in the DMZ. However, staff also have the additional requirement that if they login to the SSH server from the Internet (e.g. while they are at home or travelling), they can then initiate a 2nd SSH connection from the SSH server to their office computer on the staff subnet (this assumes staff office computers also have SSH servers running). Staff can use this to remotely access their office PCs from home. Students (and others outside the institute) are not allowed to do this.
4. The Head of the institute finds performing two SSH connections to access their office computer too difficult. They have requested that they be able to directly SSH from their home computer to their office computer, bypassing the SSH server in the DMZ. The Head has a fixed IP at home: 103.3.63.106.
Considering the above information, answer the following questions:
a) Draw a diagram illustrating the network. Although there may be many computers in the staff and student subnets, for simplicity you only have to draw three computers in the staff subnet and three computers in the student subnet. One of the three in the staff subnet should be the Head's office computer. Label all computers and router interfaces with IP addresses.
b) Specify the firewall rules using the format as in the table below. You may add/remove rows as needed.
|
Rule No.
|
Transport
|
Source IP
|
Source Port
|
Dest. IP
|
Dest. Port
|
Action
|
|
1
|
|
|
|
|
|
|
|
2
|
|
|
|
|
|
|
|
3
|
|
|
|
|
|
|
|
4
|
|
|
|
|
|
|
|
...
|
|
|
|
|
|
|
c) Give a short explanation of the rules. Also identify any potential issues with the rules (that is, in practice what could go wrong when using your firewall rules) and possible solutions.
d) Consider the Port Address Translation service on the gateway router. The following table shows the addresses of packets arriving on interface ifint at the router. The packets are listed in order at which they arrive at the router. Complete the addresses for the packets as they are sent out on interface ifext of the router.
|
Packets arriving on ifint before PAT
|
Packets departing on ifext after PAT
|
|
Source IP
|
Source Port
|
Dest. IP
|
Dest. Port
|
Source IP
|
Source Port
|
Dest. IP
|
Dest. Port
|
|
10.2.1.45
|
50345
|
103.67.45.1
|
80
|
|
|
|
|
|
10.2.1.67
|
49321
|
73.18.9.3
|
443
|
|
|
|
|
|
10.2.1.45
|
50345
|
103.67.45.1
|
80
|
|
|
|
|
|
10.2.2.16
|
49321
|
63.108.4.13
|
80
|
|
|
|
|
|
10.2.1.83
|
54693
|
73.18.9.3
|
443
|
|
|
|
|
|
10.2.2.16
|
52987
|
103.67.45.1
|
80
|
|
|
|
|
Question 4 - Vulnerability Research
Objective: research advanced malware and identify the basic techniques they are built upon.
New malware is being discovered regularly by security researchers. As the malware is discovered, detection techniques are developed, but then malware developers improve their malware to avoid detection. This cycle has led to very advanced malware, using a combination of basic techniques. One widely publicised malware was Stuxnet. In 2010 Stuxnet was discovered to have used various techniques to infect industrial control systems (which were not connected to the Internet), with the possible purpose of shutting down facilities in Iran that developed nuclear material. The techniques used have been linked to other attacks, and the Equation Group.
Your task is to gain a basic understanding of how Stuxnet worked and recommend procedures for avoiding similar types of advanced malware. A detailed explanation of Stuxnet is provided by Symantec at:
https://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w3 2_stuxnet_dossier.pdf
This has sufficient information for you to learn about Stuxnet for this task, however you may use other resources as well.
a) Summarise how Stuxnet worked. Refer to the concepts learnt in lectures in your description (e.g. malware traits of circulation, infection, concealment, payload; was it a logic bomb? did it use spam? ...).
b) Provide a set of recommendations for how to avoid being impacted by Stuxnet or similarly complex malware. For example, consider you are the Security Manager in a company with large and important industrial control systems (e.g. power companies, defence facilities, manufacturing) and you need to produce a concise list of recommendations to avoid Stuxnet like attacks to the Chief Information Security Officer. The recommendations should be justified, e.g. "Recommendation 1: do this because of this reason". The number of recommendations should be appropriate for the number of different techniques Stuxnet uses.
Although there are no strict length requirements, part a) could be answered in ½ to 1 page, while part b) could be answered with a list of multiple items with each item containing several sentences.