Reference no: EM13897734
Your company just recently installed new routers onto the network and has asked you to design the appropriate security to prevent unwanted traffic and to prevent illegal activities from occurring. Your job in this project is to use the diagram below and the criterion set by the company to come up with the proper command structure to create the access control lists. Document the steps you used to create and determine (justify) the usage of your ACL and is part of process of implementation of a new security feature. Remember to include what type of access list you created, where you applied, and why. Below is a diagram of the current network and some specific requests from the company.
\Some specific request from the company
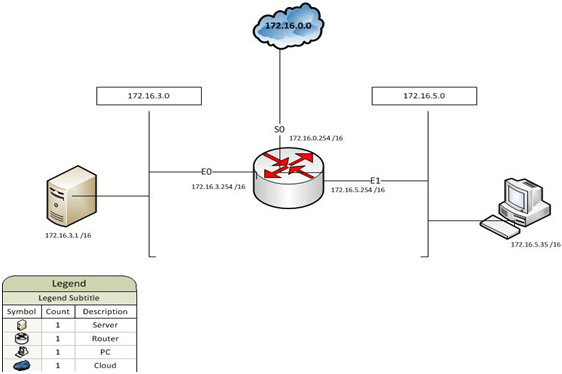
1. The company wants to prevent all traffic that is not part of the internal network (172.16.0.0 /16) from traveling out of the Ethernet interfaces.
2. They also want to prevent host 172.16.5.35 from accessing the Internet.
3. Consideration needs to be made to prevent Telnet, ftp, and ability to ping from outside of the network.
4. The 17.16.3.0 segment houses all of the sales information. The company wants to prevent access from other networks to that segment.
Write an eight to ten (8-10) page paper in which you:
1. Re-create the diagram above and add the needed ACL to the appropriate port by using Visio or similar drawing program.
2. Create Standard Access Lists.
3. Create Extended Access Lists.
4. Apply the access list correctly.
5. Justify the ACL and describe each purpose.
Your assignment must follow these formatting requirements:
1. Be typed, double spaced, using Times New Roman font (size 12), with one-inch margins on all sides; references must follow APA or school-specific format. Check with your professor for any additional instructions.
2. Include a cover page containing the title of the assignment, the student's name, the professor's name, the course title, and the date.
The cover page and the reference page are not included in the required page length.
The specific course learning outcomes associated with this assignment are:
1. Demonstrate the use of operating system commands to monitor, control, and configure Internetworking environments.
2. Describe organizational security considerations in an Internetworking environment.
3. Use technology and information resources to research issues in internetworking.
4. Write clearly and concisely about basic internetworking topics using proper writing mechanics and technical style conventions.