Reference no: EM131413406
Hands-On Project 10-5: Denying Access to Specific Sites for Specific Users
Objective: Configure rule parameters to limit user access to Web functions.
Description: Although Internet access has become a necessity for many organizations, this access also presents problems. Employees might abuse their Internet access and hurt productivity by using social networking sites, or they could even endanger the organization by performing illegal acts through Internet access. TMG allows very specific restrictions to be configured. In this project, you create detailed restrictions for a single user.
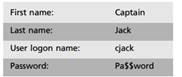
1. On the Windows Server 2008 domain controller, create a user with the following attributes:
2. In TMG, click Web Access Policy in the left frame. Click Create Access Rule in the right frame.
3. In the welcome window, type Web Abusers in the Access rule name text box, and click Next.
4. In the Rule Action window, verify that Deny is selected, and click Next.
5. In the Protocols window, HTTP and HTTPS are already selected. Click Add, expand All Protocols, select FTP, and click Add. Click Close, and click Next.
6. In the Access Rule Sources window, click Add, expand Networks, select Internal, and click Add. Click Close, and click Next.
7. In the Access Rule Destinations window, click Add, click the New menu, and click Domain Name Set. In the Name text box, type Social Networking Sites. Click Add, rename the New Domain as facebook.com, and click OK. From the Domain Name Sets list, select Social Networking Sites, and click Add. From the New menu, click Address Range. In the Name text box, type Linux Web Server. In both the Start Address text box and the End Address text box, type the IP address of the Linux Web server. Click OK. In the Address Ranges list, select Linux Web Server, and click Add. Click Close. Click Next.
8. In the User Sets window, select All Users, and click Remove. Click Add, and click the New menu. In the welcome window, type Web Abusers in the User set name text box, and click Next. In the Users window, click Add, and click Windows users and groups. In the Select Users or Groups window, click the Locations button. If the Windows Security window appears, enter administrator as the username and Pa$word as the password, and click OK. In the Locations window, expand Entire Directory, select Teamx.net, and click OK. In the Enter the object names to select text box, type cjack, and click Check Names. Captain Jack's name should appear underlined. Click OK, click Next, and click Finish. In the Add Users window, select Web Abusers, click Add, click Close, and click Next. Click Finish. Click Apply. In the Change description text box, type Web Abusers created and enabled. Click Apply, and click OK.
9. From the Windows 7 system, log on to the domain as Captain Jack. Open a Web browser and attempt to access the Linux Web server, as you did in Step 15 of Hands-On Project 10-3. Your attempt should fail. If your systems were connected to the Internet, access to Facebook and FTP sites would also be denied. 10. Log off the Windows 7 system, and log on as another domain user. Attempt to access the Linux Web server again. This attempt should succeed.
10. Log off all computers.
|
Write a one to two page paper summarizing your findings
: Write a one to two page paper summarizing your findings. The written summary should be double-spaced using 12-point Times New Roman font.
|
|
Nonprofit organization-differences from for-profit
: Discuss briefly, but fully, a definition of a nonprofit organization and differences from a for-profit organization.
|
|
Identify and describe the stages of team development
: Identify and describe the stages of team development.How might stronger team skills benefit you? How might you use teamwork skills in your job? Provide specific examples.What is it like to participate in a virtual meeting, such as web-based, teleconf..
|
|
Administration and politics dichotomy
: What are the advantages and disadvantages of using such a dichotomy today as a way to advance that field of study? Support your case with examples.
|
|
Create a user with the following attributes
: In the Protocols window, HTTP and HTTPS are already selected. Click Add, expand All Protocols, select FTP, and click Add. Click Close, and click Next.
|
|
Describe the discrepancy juxtaposing the theory and practice
: Every HR manager has a list of "best practices" regarding personnel policies, but does the knowledge of these ideal practices always translate into their successful implementation? Unfortunately, there is often a discrepancy between an ideal pract..
|
|
Measure the performance of a warehouse
: Provide a critical assessment based on the above article text readings, scholarly research, and personal experience. Cite your resources using APA format.
|
|
What are the three overall conclusions you have drawn
: Based on all the information you are able to recover and your review, what are the three overall conclusions you have drawn about the health delivery sector you chose?
|
|
Adopting a centralized distribution system
: Inventory can be reduced by (a) reducing order quantity, (b) adopting a centralized distribution system, (c) using common parts for different products, and (d) reducing lead time. Explain how inventory can indeed be reduced by each of the above fo..
|