Reference no: EM133536039
Part A - Hands-On Networking
Overview:
The purpose of this exercise is to familiarize you with emerging network technologies, like SDN, and to reinforce your understanding of the network protocol stack. Using the Mininet virtual network manager to create a simple virtual network, implementing a set of simple performance limitations, while using the Floodlight SDN controller. Note that Mininet is not a traditional network simulator; rather, it is a tool to instantiate lightweight virtual hosts and connect them using a set of virtual switches.
Students are encouraged to proactively find the solutions to the exercise challenges on their own and contact the instructor/TA in case they find requirements unclear or under-specified. A Canvas Discussion is available to enable conversation between students (and the instructor/TA). While students can discuss challenges, each individual must submit their own work.
Part 1. Mininet and Floodlight Setup:
Project Floodlight (an openSDN project) provides a pre-configured virtual machine (VM) which includes both the Floodlight software and the Mininet virtual network emulator. This enables users to instantiate a virtual SDN using Mininet and to control the network using an instance of Floodlight. The Floodlight VM also includes the Eclipse IDE and Wireshark. You can run them by browsing in the Ubuntu GUI or through the terminal.
To run the Floodlight/Mininet VM, you need to install VirtualBox, a free virtualization software available. The Floodlight VM may run within other virtualization technologies, but for grading purposes students must use VirtualBox.
Once VirtualBox is installed, download the Floodlight VM following the instructions. Skip the section titled "Update Floodlight", as it will cause issues within your VM.
Mininet comes pre-installed in the Floodlight VM. You are required to read through the Mininet walkthrough to familiarize yourself with this complex tool. It is recommended that you complete the Mininet walkthrough to ensure your grasp of the concepts.
Part 2. Create a Network Topology
Step 1: Using python, write a script to create a simple "balanced" data-center-like topology (e.g., a tree topology) with eight hosts, seven switches and one domain controller. The figure below depicts an example of a tree topology with a depth of 2 and a fanout of 2 switches/hosts per level:
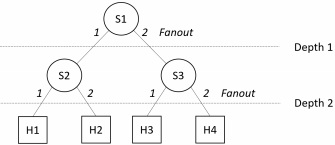
Step 2: Modify your script to include to following performance settings of 10Mbps, 5ms delay between most links and 100Mbps and 10ms delay between switch 4 and its hosts.
1. Your python script to complete Part 2 - Step 1
2. Your python script to complete Part 2 - Step 2
Part B - Theoretical Q&A
Questions:
A. One of your classmates, Josh, has pointed out that it is wasteful to end each frame with a flag byte and then begin the next one with a second flag byte. One flag byte could do the job as well, and a byte saved is a byte earned. Do you agree? Explain your answer.
B. Given a sixteen-bit message using Hamming Code, how many check bits are needed to ensure that the receiver can detect and correct a single-bit error? Show the bit pattern transmitted for the message 1101001100110101. You can assume that even parity is used.
C. Given the transmitted message 1001 1100 1010 0011; what is the value of the 4-bit checksum?
Chap 4: 13, 20, 24, 25, and 31 (worth 6 points per question)
V5: 11, 18, 22, 23, and 27
D. Given a wireless network with 5 stations, A-E. Station A can communicate with all other stations. B can communicate with A, C, and E. C can communicate with A, B, and D. D can communicate with A, C, and E. E can communicate with A, D, and B.
a. When A is sending to B, what other communications are possible?
b. When B is sending to A, what other communications are possible?
c. When B is sending to C, what other communications are possible?