Reference no: EM131215426
This is a set of simple matrix manipulations.
a. Create a five by six matrix, A, that contains random numbers between 0 and 10.
b. Create a six by five matrix, B, that contains random numbers between 0 and 10.
c. Find the inverse of matrix A*B and store it in the variable, C.
d. Without iteration, create a new matrix D that is the same as A except that all values less than 5 are replaced by zero.
e. Using iteration, create a new matrix F that is the same as A except that all values less than 5 are replaced by zero.
f. Create a new matrix G that is the matrix A with the columns reversed.
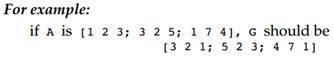
g. Find the minimum value amongst all the elements in A and store your answer in the variable H.
|
The farming industrys impact on the environment
: Prepare a paper on "The farming industry's impact on the environment: who is the biggest culprit?" - Agriculture or farming is the world's largest employment generating industry. Green revolution in 1960's and 70's increased the agricultural produc..
|
|
Find the probability that the roots are real
: Find the probability that the roots are real. - Find the probability that the roots are complex. - Find the probability that the roots are equal.
|
|
Calculate the ripple factor for each given filter
: Calculate the ripple factor for each filter. Data section will include two circuits, six screenshots including measured values, four ripple factor calculations. (Nothing submitted should be hand-written)
|
|
What is the variance of the gaussian pdf
: Find the PDF of the magnitude- What is the variance of the Gaussian PDF that approximates the PDF of the phase angle.
|
|
Create a new matrix g that is the matrix a
: Since the numbers will have different magnitudes, use plotyy to plot the linear values on the right hand axis.
|
|
Independent nation and supply
: The Confederate belief during the Civil War that their cotton was so important to the British and French economies that those governments would recognize the South as an independent nation and supply it with loans and arms.
|
|
Missouri compromise line to the california border
: A plan proposed by Senator John J. Crittenden for a constitutional amendment to protect slavery from federal interference in any state where it already existed and for the westward extension of the Missouri Compromise line to the California border..
|
|
Which do you feel is the biggest challenge and why
: Identify three challenges that a U.S. business person may encounter in a global environment. Which do you feel is the biggest challenge and why?
|
|
Find the characteristic function
: Find the characteristic function associated with this complex Gaussian random variable, - Do you get the same (or different) results as with a real Gaussian random variable.
|