Reference no: EM131412072
Hands-On Project 13-3: Collecting a Hardware and Software Inventory
Objective: Create a hardware and software inventory of your network and save it to a file.
Description: Creating a complete hardware or software inventory of your network can be a daunting task. Several methods, from simple VBScripts to high-end software programs, can automate this chore. In this project, you use Network Asset Tracker from MIS Utilities to gather hardware and software data about your computer and save it to a file.
1. Start your Web browser. Go to www.misutilities.com/network-asset-tracker/index.html.
2. Click the DOWNLOAD tab. Save the natracker.exe file to your desktop.
3. Right-click natracker.exe, and click Run as Administrator. In the User Account Control window, click Yes.
4. In the Language Selection window, click Next.
5. In the welcome window, click Next.
6. In the Readme Information window, click Next.
7. In the License Agreement window, click Yes, I agree with all the terms of this license agreement, and click Next.
8. In the Destination Folder window, click Next.
9. In the Select Components window, click Next. In the Program Group window, click Next.
10. In the Ready to Install the Program window, click Next.
11. In the Installation Complete window, click Finish.
12. Click Start, click All Programs, click Network Asset Tracker, and click Network Asset Tracker to start the program. If a User Account Control window appears, click Yes. Click Close to dismiss the Tip of the Day.
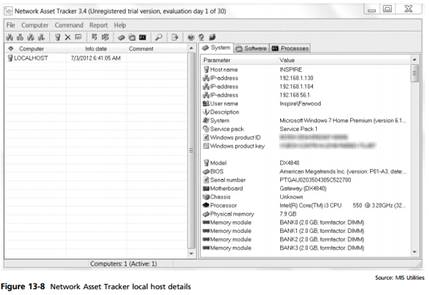
13. Right-click the LOCALHOST computer icon, and click Get/Update Info. A window like the one shown in Figure 13-8 displays details about your system.
14. Click the Report menu, and click System Information. Under Type of report, click the List option button, and click Ok.
15. Click Export and save the System Information file to your desktop. Click OK in the Information window, and click Close.
16. From your desktop, double-click the System Information.html file. Read through the file to examine the information that was gathered. When you are finished, close the file.
17. Click the Report menu, and click Software Information. Click Ok.
18. Click Export and save the Software Information file to your desktop. Click OK in the Information window, and click Close.
19. From your desktop, double-click the Software Information.html file. Read through the file to examine the information that was gathered. When you are finished, close the file.
20. Click the File menu, and then click Exit to close the program.
|
Find the margins of error associated with a given chance
: If you have studied the central limit theorem, find the margins of error associated with a chance of .90 and a chance of .95. Compare these values with those calculated in step 2.
|
|
Shares of abc corporation stock
: Mr. R. owns20,000 shares of ABC Corporation stock. The company is planning to issue a stock dividend. Before the dividend Mr. R. owned 10 percent of the outstandingstock, which had a market value of$200,000, or$10 per share. Upon receiving the 10 ..
|
|
What are primary and secondary markets
: What are primary and secondary markets? What is the difference between a primary market and a secondary market? Your response should be at least 200 words in length.
|
|
Determining the average tax rate
: Their capital structure includes both preferred and common stock and they paid $10,000 and $15,000 respectively in dividends. Given all that I need you to tell me three things: What was their federal tax bill, what was their average tax rate, what ..
|
|
Create a hardware and software inventory of your network
: Creating a complete hardware or software inventory of your network can be a daunting task. Several methods, from simple VBScripts to high-end software programs, can automate this chore. In this project, you use Network Asset Tracker from MIS Utili..
|
|
Determining the foreign exchange risk
: 1. Comment on the following statement: If you have a lot of foreign holdings scattered around the world, foreign exchange risk is not much of a problem because the various translation gains and losses all average out to zero in the long run.
|
|
Chemtec marginal tax rate on earnings
: Assume that Chemtec's marginal tax rate on earnings is 35%. Assuming that all of these cash flow occur at the end of the first year, what is the first year's free cash flow?
|
|
Comment on the given situation
: Your friend is convinced that her dream was a warning and that she should have told someone in authority. Comment on this situation.
|
|
Receive for the plant for the divestiture to beprofitable
: If the plant has average risk and Goodyear plans to maintain a constantdebt-equity ratio, whatafter-tax amount must it receive for the plant for the divestiture to beprofitable? A divestiture would be profitable if Goodyear received more than $not..
|