Reference no: EM132605606
CP3404 Information Security - James Cook University
Aim: This assignment is designed to help you improve your critical thinking and problem solving skills, as well as your information literacy skills (i.e. the ability to select and organise information and to communicate it effectively and ethically).
1. Using the web, find out who Kevin Mitnick was. What did he do?
Who caught him?
Write a short summary of his activities and why he is famous.
2. One-Time Pad (OTP) - An unbreakable cryptographic system
Use the Internet to search OTPs; who was behind the initial idea, when they were first used, in what application they were found, how they are used today, etc. Then visit an online OTP creation site such as www.braingle.com/brainteasers/codes/onetimepad.php and practice creating your own ciphertext with OTP. Exchange your OTPs with other students to see how you might try to break them. Would it be practical to use OTPs? Why or why not? Write a short summary on your findings.
3. Cryptanalysis of Substitution Ciphers:
In this question you learn a classical monoalphabetic (substitution) cryptographic system, and are required to cryptanalysis a given cryptogram.
In substitution ciphers, a permutation of the alphabet is chosen as the cryptogram of original alphabet. That is, every letter of the plaintext substitutes by corresponding letter in the permuted alphabet. For example,
a b c d e f g h i j k l m n o p q r s t u v w x y z c
o d k s z r g e l u y a f m v p h i n w t b j q x
Figure 1: A possible permutation of English alphabet
is one of such permutation, in which letters a, b, c, , y, z from the plaintext are substituted by corresponding letters c, o, d, , q, x respectively. Since remembering permutation is not easy, one may employ a keyword and use a table to generate the permuted alphabet. Let CRYPTOGRAPHY be the keyword. The permuted alphabet can be obtained as follows.
• Choose a 6 × 5 table/matrix, i.e., a table with 6 rows and 5 columns.
Write down the secret keyword in cells (1, 1), (1, 2), , one letter in each cell, but skip repeated letters. Figure 2 shows how ‘CRYPTOGRAPHY' (as a keyword) written down in the table.
Write alphabet letters (in order) from the first available cell after keyword, but skip all letters that are already written in the table. You will come out with Table 3.
The permuted alphabet, which will be used to generate the cryptogram, can be obtained by simply reading the content of Table 3 in columns order (see Figure 1).
Figure 2: CRYPTOGRAPHY is the Keyword
Your Task:
Cryptanalysis of an information system is the study of mathematical techniques for attempting to defeat information security services.
A cryptographic system is said to be breakable if a third party (i.e., cryptanalyst), without prior knowledge of the key, can systematically recover plaintext from corresponding cipher- text within an appropriate time frame.
In this question, you are required to determine the plaintext and the keyword associated to the given cryptogram. Note that brute force attack (i.e., searching all possible keys) in order
|
C
|
R
|
Y
|
P
|
T
|
|
O
|
G
|
A
|
H
|
B
|
|
D
|
E
|
F
|
I
|
J
|
|
K
|
L
|
M
|
N
|
Q
|
|
S
|
U
|
V
|
W
|
X
|
|
Z
|
|
|
|
|
Figure 3: Table for permuting alphabet
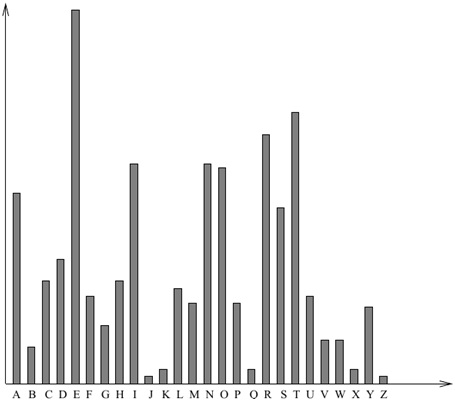
Figure 4: Letter frequency in English texts
to find the keyword is not efficient. However, letter frequency (see Figure 4) attack is an efficient tool for breaking substitution ciphers.
In the following you can find 10 cryptograms, where the breaks are genuine breaks between English words. You are required to decipher the cryptogram that matches with your Student- ID.
Attachment:- Information Security.rar