Reference no: EM132010107
Securing Company Network - Network Topology
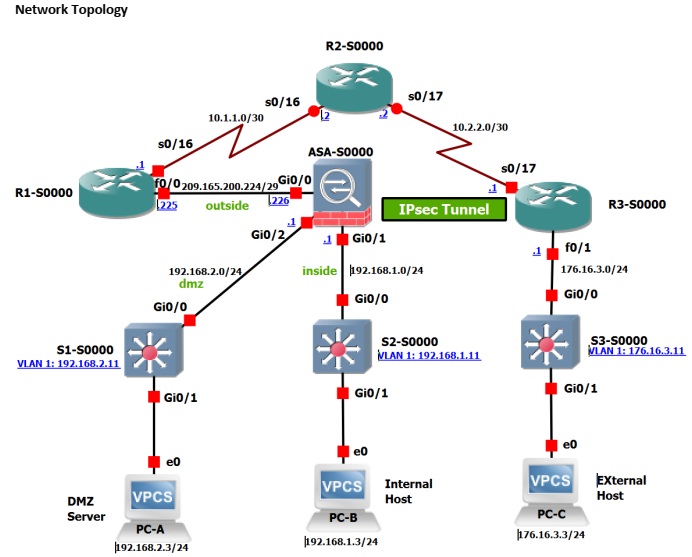
Note: ISR G1 devices have Fast Ethernet interfaces instead of Gigabit Ethernet Interfaces.
In this lab, you will perform the following tasks: Part 2: Configure Basic Device Settings
Part 3: Configure Secure Router Administrative Access
- Configure encrypted passwords and a login banner.
- Configure the EXEC timeout value on console and VTY lines.
- Configure login failure rates and VTY login enhancements.
- Configure Secure Shell (SSH) access and disable Telnet.
- Configure local authentication, authorization, and accounting (AAA) user authentication.
- Secure the router against login attacks, and secure the IOS image and the configuration file.
- Configure a router NTP server and router NTP clients.
- Configure router syslog reporting and a syslog server on a local host.
Part 4: Configure a Zone-Based Policy Firewall and Intrusion Prevention System
- Configure a Zone-Based Policy Firewall (ZPF) on an ISR using the CLI.
- Configure an intrusion prevention system (IPS) on an ISR using the CLI.
Part 5: Secure Network Switches
- Configure passwords and a login banner.
- Configure management VLAN access.
- Secure access ports.
- Protect against Spanning Tree Protocol (STP) attacks.
- Configure port security and disable unused ports.
Part 6: Configure ASA Basic Settings and Firewall
- Configure basic settings, passwords, date, and time.
- Configure the inside and outside VLAN interfaces.
- Configure port address translation (PAT) for the inside network.
- Configure a Dynamic Host Configuration Protocol (DHCP) server for the inside network.
- Configure administrative access via Telnet and SSH.
- Configure a static default route for the Adaptive Security Appliance (ASA).
- Configure Local AAA user authentication.
- Configure a DMZ with a static NAT and ACL.
- Verify address translation and firewall functionality.
Part 7 Configure a DMZ, Static NAT, and ACLs on an ASA
Part 8: Configure ASA Clientless SSL VPN Remote Access Using ASDM
- Configure a remote access SSL VPN using the Cisco Adaptive Security Device Manager (ASDM).
- Verify SSL VPN access to the portal.
Part 9: Configure a Site-to-Site VPN between the ASA and ISR
- Configure an IPsec site-to-site VPN between the ASA and R3-S0000 using ASDM and the CLI.
- Activate and verify the IPsec site-to-site VPN tunnel between the ASA and R3.
BACKGROUND
This comprehensive pratical is divided into parts. The parts should be completed sequentially. In Part 1, you will configure the basic device settings. In Part 2, you will secure a network router using the command-line interface (CLI) to configure IOS features, including AAA and SSH. In Part 3, you will configure a ZPF and IPS on an ISR. In Part 4, you will configure a network switch using the CLI. In Parts 6 and 7, you will configure the ASA firewall functionality and clientless SSL VPN remote access. In Part 8, you will configure a site-to-site VPN between the ASA and R3.
Note: The router commands and output in this lab are from a Cisco 1941 with Cisco IOS Release 15.4(3)M2 (UniversalK9-M). Other routers and Cisco IOS versions can be used. See the Router Interface Summary Table at the end of the lab to determine which interface identifiers to use based on the equipment in the lab. Depending on the router model and Cisco IOS version, the commands available and output produced might vary from what is shown in this lab.
The ASA used with this lab is a Cisco model 5505 with an 8-port integrated switch, running OS version 9.2(3) and the Adaptive Security Device Manager (ASDM) version 7.4(1) and comes with a Base license that allows a maximum of three VLANs.
Note: Before beginning, ensure that the routers and switches have been erased and have no startup configurations.
Task 1: Configure Basic Device Settings
The desktop system assigned to you serves as an end-user terminal. You access and manage the lab environment from the student desktop system using GNS3 Software.
Students should perform the steps in this task individually.
In Part 1 of this lab, you set up the network topology and configure basic settings, such as the interface IP addresses, static routing, device access, and passwords.
Part 2: Configure Secure Router Administrative Access (Chapters 2 and 3)
You will use the CLI to configure passwords and device access restrictions.
Task 1: Configure Settings for R1-S0000 and R3
Task 2: Configure the SSH Server on R1-S0000 and R3
Task 3: Secure against Login Attacks and Secure the IOS and Configuration File on R1 (Optional)
Task 4: Configure a Synchronized Time Source Using NTP
R2-S0000 will be the master NTP clock source for R1-S0000 and R3.
Optional: Task 5: Configure Syslog Support on R3-S0000 and PC-C
Part 4: Configure a Zone-Based Policy Firewall and Intrusion Prevention System (Chapters 4 and 5)
In Part 4, you will configure a ZPF and IPS on R3-S0000 using the CLI.
Task 1: Configure a ZPF on R3-S0000 using the CLI
Task 2: Configure IPS on R3-S0000 using the CLI.
Part 5: Secure Network Switches (Chapter 6)
Note: Not all security features in this part of the lab will be configured on all switches. However, in a production network all security features would be configured on all switches.
Part 6: Configure ASA Basic Settings and Firewall (Chapter 9) (Optional)
Task 1: Prepare the ASA for ASDM Access
Task 2: Configure Basic ASA Settings Using the ASDM Startup Wizard (Optional)
Task 3: Configuring ASA Settings from the ASDM Configuration Menu
Task 4: Modify the Default Modular Policy Framework using ASDM.
Part 7: Configuring a DMZ, Static NAT, and ACLs (Chapter 10) (Optional)
In Part 6 of this lab, you configured address translation using PAT for the inside network using ASDM. In this part, you will use ASDM to configure the DMZ, Static NAT, and ACLs on the ASA.
To accommodate the addition of a DMZ and a web server, you will use another address from the ISP range assigned (209.165.200.224/29). R1-S0000 G0/0 and the ASA outside interface already use 209.165.200.225 and
.226. You will use public address 209.165.200.227 and static NAT to provide address translation access to the server.
Part 8: Configure ASA Clientless SSL VPN Remote Access (Chapter 10)
In Part 8 of this lab, you will use ASDM's Clientless SSL VPN wizard to configure the ASA to support clientless SSL VPN remote access. You will verify your configuration by using a browser from PC-C.
Part 9: Configure a Site-to-Site IPsec VPN between R3-S0000 and the ASA. (Chapters 8 & 10)
In Part 9 of this lab, you will use the CLI to configure an IPsec VPN tunnel on R3-S0000 and use ASDM's Site-to-Site Wizard to configure the other side of the IPsec tunnel on the ASA.
Task 1: Configure the Site -to-Site IPsec VPN Tunnel on R3
Task 2: Configure Site -to-Site VPN on ASA using ASDM
Task 3: Test the Site -to-Site IPsec VPN Connection between the ASA and R3
Attachment:- Assignment.rar