Reference no: EM131103298
Assignment No. 1: Computer Network Security for a Home/Small scale Network.
Learning outcomes:
1. Identify the various threats and risks in a small scale network
2. Describe and compare a number of different techniques to secure a network
3. Analyse, evaluate and apply various techniques currently used to protect a network.
4. Design a secure network system
Introduction
In today's world computers are used for everything from banking and investing to shopping, games, leisure and communicating with others, therefore online security is of a concern for clients or users, organisations and the administrators trying to protect sensitive data located on these computers.
Computer security has become a very important issue that needs to be dealt with at every level of a network or system: physical, user-based, service-based, host-based and network-based to secure data, protect privacy and prevent frauds. Network security involves protecting all the resources on the network from threats (physical, packet sniffers, port analysers, denial of Access, spoofing, data alteration, TCP session hijacking, virus and malicious attacks...). You must consider not only the computers on the network, but other network devices, network transmission media and the data being transmitted across the network.
Assignment Brief
You are requested to design a secure home or small scale network (Fig. 1) to satisfy the key concepts underlying computer and network security: confidentiality, integrity, availability, accountability and non-repudiation.
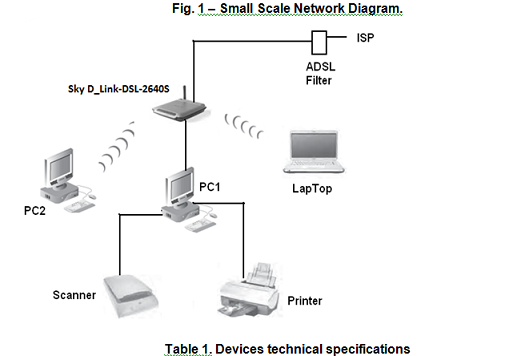
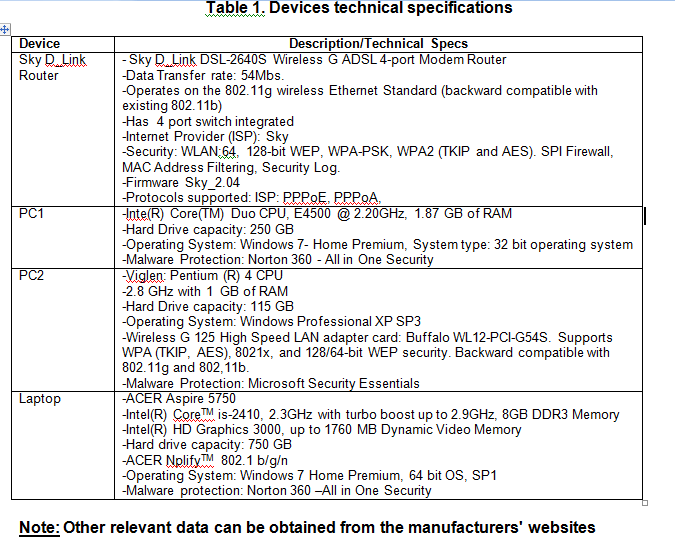
Fig. 1 shows a small home network comprising: two personal computers (PC1 and PC2), a laptop and an ADSL Modem with wireless G Router. PC1 is directly wired to the Router using an RJ45 connections crossover cable, while PC2 and the laptop are connected by wireless adapters to the router. A mobile phone, iPhone 4S, can also connect to the internet using wireless technology. The technical specifications of the devices and the details of the operating systems are given in Table 1.
The network is peer-to-peer networking to allow the users to share files and printing and scanning facilities attached to PC1.
1. Identify possible weaknesses in the network infrastructure that may make it vulnerable to attacks, accidental and intentional misuses. Assess the assets, vulnerabilities and threats to the network. Carry out a risk analysis for the data asset.
2. What are the reasonable precautions, countermeasures and risk mitigation to provide/install in order to secure the network?
3. Visiting guests need to access and connect to the internet, using their private laptops, how would you devise/design procedures to protect the network and the information contained in the devices?
4. The network owner would like to convert PC1 to a file server and would like secure access to his files from outside the network using the internet, how would you change/design the network to satisfy this requirement?
|
Define celebrity endorsements
: What Federal Trade Commission (FTC) regulations define celebrity endorsements? What is the recommended designation a celebrity endorser should include on any tweets or posts via social media to disclose his or her relationship with a company whose..
|
|
College tuition at the beginning of the academic year
: Here is the deal: You can pay your college tuition at the beginning of the academic year or the same amount at the end of the academic year.
|
|
Cost effectiveness of solutions
: The last step in determining potential solutions is to conduct external research. Using Internet and industry resources, research ways that other companies have addressed this issue or one very similar to it. Look for specific information related ..
|
|
Technical skills among first-line supervisors
: 1. What arguments would Support UniTech's focus on technical skills among first-line supervisors? What arguments could be made against that focus? What are the pros and cons of periodically sending top managernent out to work alongside non-mana..
|
|
Computer network security for a home
: Assignment No. 1: Computer Network Security for a Home/Small scale Network.Learning outcomes:1. Identify the various threats and risks in a small scale network2. Describe and compare a number of different techniques to secure a network3. Analyse, eva..
|
|
Exceeded market demand
: If you were an operations manager, what would you do if market demand exceeded the production capacity of your manufacturing facility? What action would you take if the production capacity of your manufacturing facility exceeded market demand?
|
|
How did what you learned from the interview
: How might you be able to use what you learned from the interview in your future work with children and families? (These might be specific tips and strategies for helping a child who is learning English, or a heightened awareness of the problems an..
|
|
Strategic controls and financial controls
: What are the differences between strategic controls and financial controls, and how do they relate to organizational structure? What is the importance of these differences?
|
|
How can it has a output
: I wonder what is the field "out" use for? Instructors comment it "// stream where Target will prints its output". Target is not a function, how can it has a output? I also confused about "std::ostream &out = std::cout", don't understand what is it..
|