Reference no: EM132918806
MITS5004 IT Security - Victorian Institute of Technology
Question 1 a) Compute the Public and Private Key using the RSA Algorithm, assuming the selected prime numbers p and q are 3 and 11 respectively.
b) Critically analyse the three techniques, which could be employed to authenticate a message, using a hash function.
Question 2 Consider the home network shown in Figure 1. As a Master of IT student, you are required to proposeat least 3 security techniques, which could be employed to secure the home network, justify your answer.
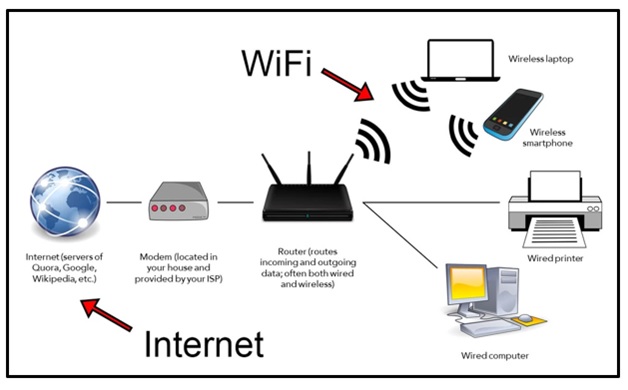
Figure 1. Home Network
Question 3
In late September 2019, a number of hospitals and health clinics across the Barwon, Gippsland and South Western regions of Victoria were targeted by a ransomware incident which stemmed from a shared Managed Service Provider (MSP) that had been infected with ransomware. In order to quarantine the spread of ransomware across the networks, the hospitals isolated and disconnected a number of systems from the internet. As a result, access to patient records and contacts, as well as scheduling and financial management systems was significantly impacted. Medical staff had to revert to manual paper-based administration, resulting in patient appointments and surgeries being rescheduled. There was no indication that the personal or medical information belonging to patients was subject to unauthorised access or exfiltration. A multi-agency incident response team was established, comprising of hospital officials, service providers and cyber security experts working alongside state and federal police and the ACSC. Compromised networks were fully remediated within a number of weeks.
a) Provide a solution, which thehealth clinics across the Barwon, Gippsland and South Western regions of Victoria could implement to improve the overall security of their systems.
b) Critique the response of the authorities to the ransomware attack.
Question 4 a) In your opinion, which steps could be taken to harden the Operating Systems and how could an IT System benefit from Operating Systems hardening? Justify your answer.
b) Differentiate between Type 1 and Type 2 Hypervisors in terms of performance, ease of use and security.
Question 5
While some people are?being sent to jail?for using open WiFi connections, an ethicist for the NY Times Syndicate is saying?there's nothing ethically wrong with piggybacking on an open WiFi connection, assuming you're not sucking up all the bandwidth. His point is that it's the responsibility of whoever owns the WiFi access point to secure it, if they don't want it used. He also points out that if you find an open connection, you should try to figure out who owns it to let them know it's open in case they want to cut it off. Of course, he leaves out the strongest argument for why there's nothing wrong with using free WiFi, assuming you're either on public property or your own property: those radio waves are no longer under the control of the access point owner once they drift off his or her property. If those radio waves reach my property, then it's not "theft" any more than if your regular radio plays loud enough that I can hear it on my property.
Answer all questions based on the above case study.
a) As a masters of Information Technology student, in your opinion is it ethical piggybacking on an open WiFi connection? Justify your answer.
b) In todays day and age if a WiFi user was to claim "he was unaware of his connection being open" would you go buy his statement? Support your argument with valid reasoning.
Attachment:- IT Security.rar
|
Discuss when disney might recognize the revenues
: Choose two of Disney's revenue sources and discuss when Disney might recognize these revenues based on your knowledge of the revenue recognition principle.
|
|
What is the purchase price of the bond of flint corporation
: On January 1, 2020, Flint Corporation purchased a $1,160,000 bond issued by ALN Ltd. What is the purchase price of the bond?
|
|
Legislative-regulatory actions for healthcare expenditures
: How might legislative and regulatory actions affect healthcare expenditures?
|
|
Explain why should higher education institution have process
: Explain why should a higher education institution have a process for evaluation of capital repair and maintenance programs? Will the plan be different
|
|
Compute the public and private key using the rsa algorithm
: Compute the Public and Private Key using the RSA Algorithm, assuming the selected prime numbers p and q are 3 and 11 respectively
|
|
What is the carrying amount of the bond on january
: What is the revised present value of the bond at January 1, 2022 using A-2 and A-4 Tables, a financial calculator, or Excel functions.
|
|
What are two specific ratios that you think are important
: The company chose to take out a $20 million loan with interest expense of $1 million per year. What are two specific ratios that you think are important
|
|
Calculate the inventory turnover ratio
: A company has sales (all on credit) of $8,30,000 and a cost of goods sold of $5,25,000. Calculate the inventory turnover ratio
|
|
What would be the percentage change in price of Bond A
: If interest rates suddenly fall by 2 percent instead, what would be the percentage change in price of Bond A and Bond B
|