Reference no: EM132507448 , Length: word count:3000
CIS114-6 Network Systems and Administration - Majan University College - University of Bedfordshire
Learning Outcome 1: Demonstrate deep and systematic understanding of system and networking concepts, including principles, technologies, and emerging trends.
Learning Outcome 2. Scientifically and critically analyse, implement and evaluate networking techniques, technologies, strategies and methodologies used in industry. Apply analytical and problem-solving skills in order to select and implement networking solutions appropriate to multiple organisational and environmental contexts.
Your Problem is to implement a virtualised environment-based solution demonstrating the operation of a VPN operating in site-to-site (Tunnel mode). Your virtual machines (VMs) requirements must include 2 VyOS routers (fully configured using the VyOS router own commands - similar to Juniper and Cisco routers commands
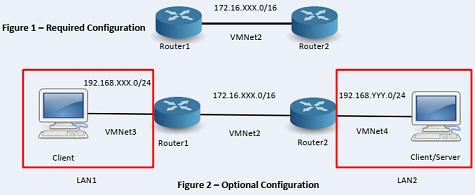
Figure 2 shows an optional configuration where additional XP VMs are to be used to demonstrate the VPN operations in both site-to-site and remote VPN (Tunnel and Transport modes) with additional Wireshark captures to be performed from one of the XP VMs.
Use of a command line sniffer such as tcpdump should is required on the networks to demonstrate the mode of operation.
You are required to either build the VMs from scratch or use the official VyOS VM available from our FTP server (see document on BREO), Dr Ali Mansour's shared Google drive (see link on BREO).
Problem 1 Implement the topology shown in Figure 1 with fully functional routers (i.e. a network connecting the two VyOS routers).
The network should be configured, tested, demonstrated, and clearly documented (part of Problem 3) showing its full operation. Routing between the two routers must be configured using any form of routing. Details of your routing implementation must be clearly stated/shown.
Problem 2 Configure, test, and demonstrate the VPN operation.
Captured traffic must be shown to demonstrate the operation of the VPN and when the VPN is not active.
Problem 3 Technical report documenting all the work done in the previous tasks. See the points below under Documentation Requirements.
Attachment:- Network Systems and Administration.rar
|
How strict or how lenient you want to make the policies
: You have just been hired as the Security Manager of a medium-sized Financial Services company employing 250 people in New Hampshire, and have been asked.
|
|
What is the project year 0 net cash flow
: What is the project's Year 0 net cash flow? What is the project's Year 1 net cash flow?
|
|
Discussion about the topic telecommunications
: Telecommunications Topics Paper: Select a topic on either 1) The Internet of Things (Industrial Internet), 2) Cloud Computing, or 3) Security.
|
|
What would be the fixed cost per unit at an activity level
: What would be the fixed cost per unit at an activity level of 3,500 units? Assume that this level of activity is within the relevant range.
|
|
CIS114-6 Network Systems and Administration Assignment
: CIS114-6 Network Systems and Administration Assignment Help and Solution, Majan University College - University of Bedfordshire - Assessment Writing Service
|
|
What would be the approximate wacc
: This project relates to construction of a new airport in Ankara and expected cash flows are as follows. If the MIRR is 10,3%, what would be the approximate WACC
|
|
Discuss corporate success and corporate failure
: Discuss corporate success or corporate failure scenario of leader where leader either resonated or failed to resonate with culture required on global scale.
|
|
What is cost of goods sold budget for andrews company
: What is cost of goods sold budget for Andrews Company? Round your answers to the nearest dollar. I am stuck on how to calculate direct labor
|
|
Calculate the sales volume variance for variable costs
: Calculate the sales volume variance for variable costs.Static Budget, Actual budget:- sales volume, sales price, Variable cost, fixed cost.
|