Reference no: EM13869162
Why are MP3 audio files and JPEG image files so much smaller and more compressed than their lossless digital counterparts? The most common algorithm for compressing digitised versions of analogue sources is the Fast Fourier Transform, or FFT. Because FFTs are so widely used, computer scientists need very efficient algorithms to calculate them.
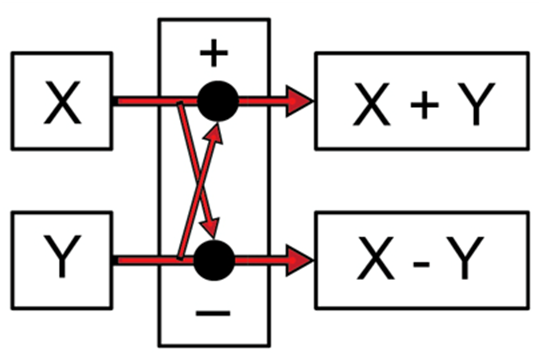
Computations arranged in ‘butterfly' formation are one way of calculating FFTs. One butterfly-shaped computational unit is shown in Fig. 1. The output cell on top stores the sum of two numbers, while the one on the bottom stores the difference.
Fig. 1: Simple Butterfly Diagram
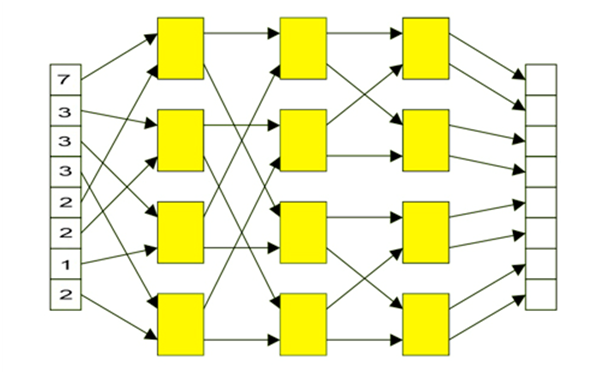
A series of such units can be organized to perform multiple operations in parallel, as shown in Fig. 2, which uses 12 of the units shown in Fig. 1.
Fig 2.: Multiple Butterfly Diagram
Submit a paper in which you solve the following problem:
• Assume a computational time for each butterfly in Fig. 1 to be 3 seconds. Compute the time necessary for the arrangement in Fig. 1 to perform 12 computations (without any parallelism).
• Compute the output of the network in Fig. 2, given the 8 values shown for inputs.
• Calculate the time needed to perform the computation on the 8 values shown in Fig. 2.
• Calculate the time needed for the arrangement in Fig.2 to perform the computation on 100 8-value data sets (Hint: Exploit pipelining).