Reference no: EM131455290
Lab Project
Instructor: Prof. Fahad Saeed Teaching Assistant: Ayaz Akram
References used: 1) HCS12/9S12 An Introduction to Software and Hardware Interfacing by Han-Way Huang 2) Dragon 12 Manual
Lab Project Details
Objectives:
• Implementing the knowledge of HCS12 Assembly and microcontroller.
• Learning the use of different hardware capabilities of the Dragon EVB.
Project Rules
• The lab project counts for 35% of lab grade.
• Use of only Assembly Language is allowed.
• This project is to be done in a group of two students.
• Performance of groups in the project will be only their own, students are not allowed to copy the code and strategies used by other groups.
• Students can ask the TA for help but the help provided will be very limited, as this project is the final evaluation for this lab.
• Students can download the Code Warrior on their personal computers and work at home or off campus. They can test their codes on the Dragon EVB during the regular lab sessions.
• If any students want to use the lab facility other than lab sessions, he/she can contact the TA during office hours.
• Projects will be graded during the last lab session.
• 5 % credit is for a project report which will also be collected during the last lab session.
• Codes should be properly commented.
• Remember Google is your best friend and Book is the best resource.
Part 1
Your task is to write assembly code to initialize an array of 50 numbers in memory. Each number of the array should be a multiple of the first number ‘x' (where 1 <= x <= 10). For example if x=5, the array should be {5, 10, 15, 20, 25, ... , 245, 250}. Once the array is initialized, the next task is to search for a number 'y' in the array using 'Binary Search' algorithm. The way Binary Search algorithm works is following:
• Input: Sorted array of numbers; Number to be searched called ‘y'
1. Calculate the midpoint index of the array by taking mean of the index of the first and the last array elements. The element at mid-point index is called ‘m'.
2. If the element at the midpoint index is the desired element, the search stops by returning the index of the desired element.
3. If m is greater than y ignore the part of the array after m (including m) for further search. If m is less than y ignore the part of the array before m (including m) for further search.
4. In any case, repeat steps 1, 2, and 3 on the remaining elements of the array. Continue till an element is found or the array indexes to be searched are exhausted.
Figure 1 shows flow-chart for Binary Search algorithm.
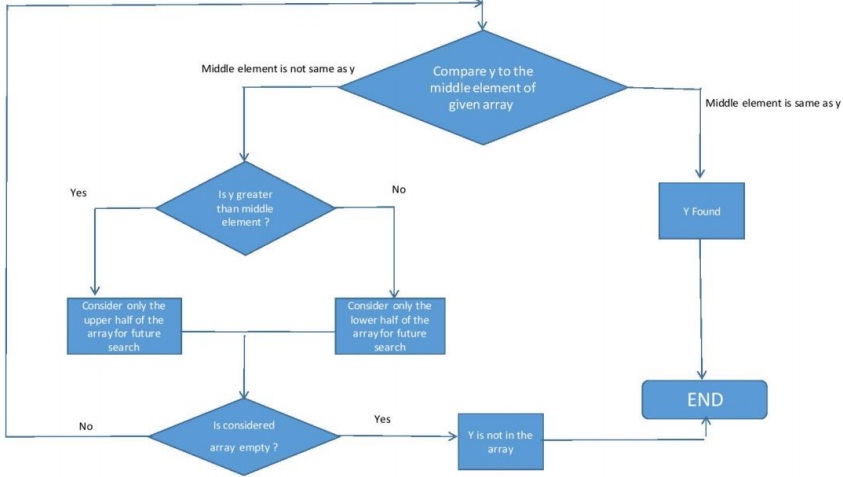
Figure 1. Flow Chart for Binary Search
Your task is to implement binary search algorithm in assembly code for any random number 'y'. While the algorithm is working, each midpoint number should be displayed on the Seven Segment Display units available on the Dragon EVB. Moreover, there should be a constant delay of 2 seconds between each update on the Seven Segment Displays. If the number being searched is present in the array the algorithm would finally stop with the number being displayed on the seven segment display. In case, the number is not in the array, your code should finally show all zeros on seven segment display (a special code indicating that the number being searched is not in the array). Your code should be generic and work for any value of y and x (within the allowed range of 1 to 10).
Part 2
In part 1, the numbers x and y will be initialized statically. In part 2, your task is to modify the code from part 1 such that the numbers x and y are initialized at run time. You will have to use DIP switches of Port H to initialize each of these numbers. You can use one of the four available push buttons (SW2-SW5) to determine when your code should read each number configured on dip switches.
Note:
• The project report should strictly follow the pattern described by the TA in the lab.
• The project report is to be written in your own words, copy pasted material will not be accepted.
• Codes copied from the internet should be properly referenced in the comments.
• Plagiarized code or report will be severely penalized and will be subject to University policies and procedures. You are responsible for making yourself aware of and understanding the University policies and procedures that pertain to Academic Honesty. These policies include cheating, fabrication, falsification and forgery, multiple submission, plagiarism, complicity and computer misuse. (The academic policies addressing Student Rights and Responsibilities can be found in the Undergraduate Catalog at https://catalog.wmich.edu/content.php?catoid=22&navoid=882 and the Graduate Catalog athttps://catalog.wmich.edu/content.php?catoid=23&navoid=938.)
If there is reason to believe you have been involved in academic dishonesty, you will be referred to the Office of Student Conduct. You will be given the opportunity to review the charge(s) and if you believe you are not responsible, you will have the opportunity for a hearing. You should consult with your instructor if you are uncertain about an issue of academic honesty prior to the submission of an assignment or test.