Reference no: EM133516901
Network Routing and Switching
Objectives
This assignment lets you demonstrate your knowledge of routing concepts by completing four tasks. You will utilise material you have studied in the unit and may extend that learning through additional reading as required. The assignment is designed to help you to achieve the unit learning outcomes listed in the unit profile.
Task 1 Routing Table construction
Consider a network scenario with four routers (labelled R1 to R4) and six subnets shown in Figure 1. A default router has been configured and all routers are fully updated.
Your task: using the table blanks provided, supply all the details of the routing table for routers R3 and R4. Arrange masks in longest-mask order, and in dotted-decimal format.
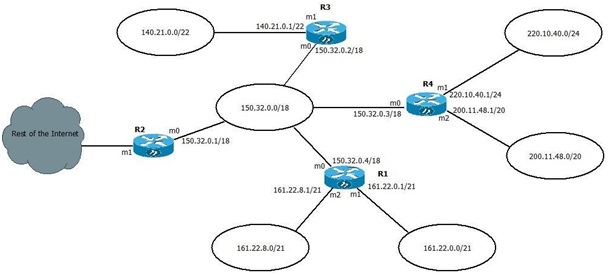
Fig. 1 Network Diagram
Task two starts on the next page.
Task 2 - Forwarding process - classless addressing
Examine and understand the forwarding process as explained in the lecture (based on Forouzan). Answer the following two questions.
Question 1: Refer to Figure 1 network diagram from Question 1. Assume that a packet arrives at router R1 with a destination address of 140.21.3.250. Explain the router's logical processing of this packet (show its calculations as well) and its forwarding decision. (1 mark for correct forwarding decision, 3 marks for clear and correct explanation including calculations).
Question 2: In the same diagram (Figure 1), assume that a packet arrives at router R2 with a destination address of 160.22.14.10. Explain the router's forwarding decision and the processes it used to reach that decision. (1 mark for correct forwarding decision, 3 marks for clear and correct explanation including calculations).
Task three starts on the next page.
Task 3 - Distance Vector 3-step routing algorithm
In Week 8, you studied the distance vector algorithm used to calculate shortest path using RIP. The diagram below was used as an aid to understand how the algorithm works - it is based on Figure 8.6 in Forouzan 6th Edn and follows the same logic.
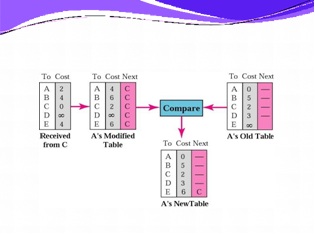
Working through this task will give you a feel for the logical processing by which Routers update each other by broadcasting a copy of their table to one another. You may find reviewing the slides and video for Week 8 helpful. If you draw the network diagram described by the tables below and update the diagram as you go, it may help you answer the questions or verify your answers.
Shown below are the initial state routing tables for Routers A, B, C, D, E, and F which all have the same destination networks listed, abbreviated to destinations A, B, C, D, E, and F with aggregated costs. For example, a cost of 6 equates to 6 hops. The solution table blanks are provided in the Answer Template.
Initial State tables for A, B, C, D, E, F
|
To
|
Cost
|
Next
|
|
A
|
0
|
---
|
|
B
|
6
|
---
|
|
C
|
∞
|
|
|
D
|
∞
|
|
|
E
|
4
|
---
|
|
F
|
∞
|
|
A' bl
|
To
|
Cost
|
Next
|
|
A
|
6
|
---
|
|
B
|
0
|
---
|
|
C
|
7
|
---
|
|
D
|
8
|
---
|
|
E
|
∞
|
|
|
F
|
5
|
---
|
B' bl
|
To
|
Cost
|
Next
|
|
A
|
∞
|
|
|
B
|
7
|
---
|
|
C
|
0
|
---
|
|
D
|
∞
|
|
|
E
|
9
|
---
|
|
F
|
∞
|
|
C' bl
|
To
|
Cost
|
Next
|
|
A
|
4
|
---
|
|
B
|
∞
|
|
|
C
|
9
|
---
|
|
D
|
∞
|
|
|
E
|
0
|
---
|
|
F
|
∞
|
|
E' bl
|
To
|
Cost
|
Next
|
|
A
|
∞
|
|
|
B
|
8
|
---
|
|
C
|
∞
|
|
|
D
|
0
|
---
|
|
E
|
∞
|
|
|
F
|
∞
|
|
' bl
|
To
|
Cost
|
Next
|
|
A
|
∞
|
|
|
B
|
5
|
---
|
|
C
|
∞
|
|
|
D
|
∞
|
|
|
E
|
∞
|
|
|
F
|
0
|
---
|
Router F' bl
To = Available network destinations
Cost = The number of hops to reach the network Next = The next hop toward the destination
∞ = infinity (network unknown, cannot be reached)
--- = no next hop or unknown
The assignment tasks:
Question 1: Router A receives an update from Router B. Process this update, showing Router A's modified and final table
Question 2: After processing B's data, Router A receives an update from Router C. Process this update, showing Router A's modified and final table.
Question 3: After a) and b) were processed, Router F receives an update from Router B. Process this update and show Router F's modified table, and its final updated table.
Question 4: What routes were unknown at the start (all tables in their initial state)? What routes are still unknown at the end (after you processed the updates in a, b & c? Express the routes in the form "A-B" = route from router A to router B.
Task 4 Fragmentation
An IP datagram 5,400 bytes long with no options arrives at a router, which determines that the next destination is an Ethernet network through which the datagram must travel. Answer the following questions, showing your calculations and reasoning.
Question 1: Assume that the router decides to fragment the packet into 4 fragments. Determine a correct size for each fragment and identify the starting byte and ending byte of each fragment.
Question 2: Calculate the fragmentation offset for each fragment.
Question 3: The total number of bytes from all 4 fragments leaving the router will be greater than the initial datagram size that arrived. Explain by how much, and the reason for this.