Reference no: EM133079177
Question 1: For x(t) = a1cos(wt + θ1) + a2cos(wt + θ2), show that:
px ≠ a12/2 + a22/2
and find the average power of x(t).
Question 2: If the energy of an energy-type signal x(t) is Ex, find the energy of x (t/a).
Question 3: If the power of a periodic signal x(t) is Px, find the average power of x (t/a).
Question 4: Determine which of the following systems are (i) LTI, (ii) Memoryless, (iii) Causal, and (iv) Stable:
(a) y(t) = a1x(t - t1) + a2x(r - t2)
(b) Y(t) = ex(t)
(c) y(t) = x(t)cos(ωot)
(d) y[n] - y[n - 1] = x[n] (Hint: represent y(t) as a summation of x[n])
(e) y(t) = 4
(0 Y[n] = lx[n]l
Question 5: Classify the following signals into energy-type signals, power-type signals, and neither energy-type nor power-type signals and calculate the energy and power for each signal:
(a) x1 = Π(t) + ∧(2t)
(b) x2[n] = ∧[n/10]
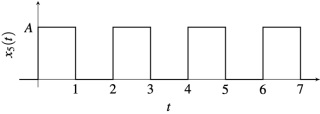
(c) x3(t) = e-jwt, -∞< t < ∞
(d) x4(t) = u(t)
|
Company aggregate project plan
: Why are R&D projects in a company's Aggregate Project Plan significantly different in type from the firm's, Derivative, Breakthrough, and Platform projects?
|
|
Explain challenge for overcoming internal consequences
: Two examples of internal consequences that may result from clients with problems with addiction. Explain one challenge for overcoming internal consequences.
|
|
What rights does Goofy have against Donald Duck
: What rights, if any, does Goofy have against Donald Duck for indemnification for Goofy's lawsuit with Mickey Mouse
|
|
Examples of internal consequences
: Two examples of internal consequences that may result from clients with problems with addiction. Explain one challenge for overcoming internal consequences. Fin
|
|
Calculate the energy and power for each signal
: Calculate the energy and power for each signal and Determine which of the following systems are (i) LTI, (ii) Memoryless, (iii) Causal, and (iv) Stable
|
|
Plot the indian rupee to the us dollar exchange rate
: Plot the Indian rupee to the U.S. dollar exchange rate over this period. For what years does the rupee appear to be pegged to the U.S. dollar? Does peg break? I
|
|
What is the maximum external price
: Concord could avoid $4000 in fixed overhead costs if it acquires the CDs externally. What is the maximum external price
|
|
Maximum willingness to pay for insurance
: Suppose that within a given city, men ages 41 and 65 fall into one of four health categories: very healthy, healthy, unhealthy, and very unhealthy.
|
|
What is Sheridan Company desired mark-up percentage
: The cost per crate is $55 and the company expects to sell 1000 crates per year. What is Sheridan Company's desired mark-up percentage
|