Reference no: EM132187107
Wireless Networks and Communication Assignment -
Part I: Encoding and error control
Sam is a computer science student and working on a new micro robot design. The robot continuously sends every two seconds a status string comprising the accelerometer reading (4 bits), ultrasound obstacle detection (6 bits), motor functionality (4 bits) and battery power level (2 bits).
a) Calculate the data rate required for robot to remote controller communication.
b) Explain 3 types of suitable encoding techniques could be used to encode the status string.
c) At a certain instance, the sensors provided data as acceleration 5 m/s2, obstacle at 48 cm, all motors working (i.e. motor functionality 1111), and battery is 75%.
i. Write the status string in binary for this instance.
ii. Represent the status string on ASK, FSK, and PSK encoding techniques.
d) Calculate the CRC for the status string derived in c) with polynomial divisor 11001101.
e) Briefly explain some other error control and flow control techniques that Sam can use to ensure the accuracy of robot control.
Part II: Multiplexing and multiple access
Multiplexing plays an important role in communication as it allows the combination of multiple streams together. Different multiplexing techniques are used for various applications.
a) Explain TDM, FDM and CDMA multiplexing techniques with suitable diagrams.
b) Main air interface in the change from 3G to 4G and WiMAX. Explain how OFDM is different from above techniques and the special feature of signals used by OFDM.
c) IEEE 802.11ac wireless LAN standard uses 40 MHz total bandwidth in OFDM scheme.
i. For 48 subscribers what should be the subcarrier bandwidth (fb)?
ii. Propose a suitable subcarrier bit time of T to achieve orthogonality?
iii. Explain how OFDM overcomes the issue of inter symbol interference (ISI)?
Part III: Wi-Fi
Prime Living is a real estate company based in Victoria and you work form them as a consultant network engineer. The company has decided to open a new office in South Eastern suburbs and the floor plan of the building is shown below. The office consists of 5 rooms and on average 8 employees work at each room. The lounge is used by both staff and customers and on average about 25 devices connect to Wi-Fi. The clients wants you to design the network for them with at least 100 Mbps data rate for all wireless connections. As resources you've got one distribution system and few access points of 10 m range.
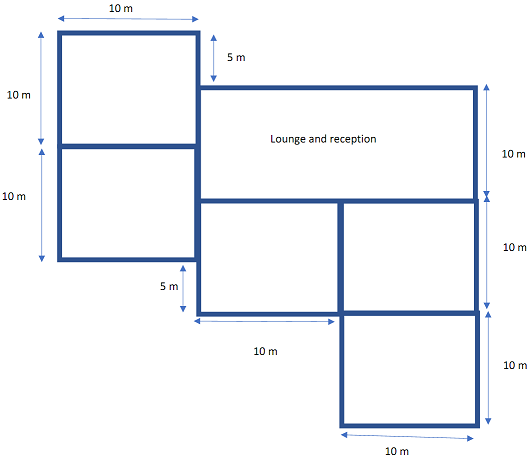
a) Design the network specifying the locations of access points and distributions system showing the backbone network.
b) Calculate the BSS and ESS sizes
c) Calculate the throughput for the DS.
d) Recommend a suitable IEEE substandard for the network and give reasons for your choice.
e) Recommend suitable security strategies for the network.