Reference no: EM132310975
Network Planning Assignment
Overview
The main objectives of this assignment are:
• To help students gain a good understanding of the IP (Internet Protocol), which is the major underlying technology of the Internet.
• To help students to understand the importance of subnet and routing of IP address.
• To encourage students to conduct an independent investigation into IP related topics from books, the Internet and through practical investigation.
Scenario
You have been appointed as a Network System Administrator by the Australian government to allocate public IP Version 4 (IPv4) addresses and build a routing table for edge routers to connect the Australian states as shown in Figure 1.
The IPv4 is an exhaustive list of IPv4 addresses for current Internet users in the world. However, in this scenario you have the liberty to use the entire available unreserved public IPv4 addresses for the Internet users in Australia.
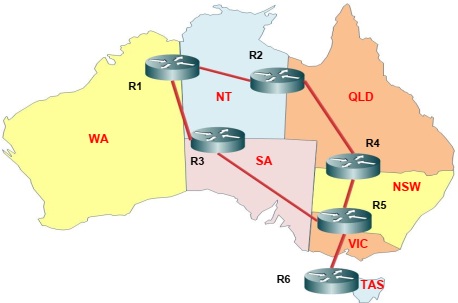
Figure 1: Edge routers R1 - R6 connecting different Australian states.
Tasks
The major task is to allocate the unreserved public IPv4 addresses to different states in Australia based on the Internet users in those states. The number of Internet users for Australian states are given below:
New South Wales (NSW) : 6 Million
Victoria (VIC) : 4 Million
Queensland (QLD) : 3 Million
Western Australia (WA) : 2 Million
South Australia (SA) : 1 Million
Tasmania (TAS) : 300 Thousand
Northern Territory (NT) : 150 Thousand
The task needs to be completed based on the following constraints and assumptions:
– Only unreserved public IPv4 address should be used for allocation.
– Each state should have unique set of addresses - no address or set of addresses can be reassigned for any other state.
– You should use only the classless IPv4 addressing in the assignment.
– The number of allocated addresses for each state should not exceed by 20% of the specified Internet users for that particular state. For instance, the allocated addresses for Tasmania should not exceed 360 Thousand addresses.
– It is allowed to use one or more subnets to achieve the number of required address for a given state.
The minor task is to create a routing table for edge routers only for the state NT, WA and SA. The task needs to be completed based on the following constraints and assumptions:
– The routing table should be minimal with no redundant routes in the table.
– Any packets from the source (NT or WA or SA) should take minimal route to reach the destination (NT or WA or SA).
– Identify the Network Interface Card Address to connect NT, WA and SA.
Learning Outcomes Assessed
The following course learning outcomes are assessed by completing this assessment:
• K1. Describe and explain the role and function of network connectivity in current computing.
• K2. Describe and explain the principles of communication in networks.
• K3. Describe the role and functionality of hardware and software entities that contribute to the network communications.
• K4. Describe and explain the protocols and interactions that implement network communications.
• K6. Describe fundamental aspects of cloud computing.
• A1. Apply networking architecture knowledge to analyze the networking needs of business.
Attachment:- Network Planning Assignment.rar