Reference no: EM132885988
1. List and briefly define categories of security services.
2. List and briefly define categories of security mechanisms
3. Using this Playfair matrix encrypt this message: "Authority without responsibility is an empty vessel."

4. Encrypt the message "meet me at the usual place at ten rather than eight o'clock" using the Hill cipher. Show your calculations and the result.
K = 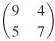
5. For a user workstation in a typical business environment, list potential locations for confidentiality attacks.
6. What is the difference between link and end-to-end encryption?
7. List ways in which secret keys can be distributed to two communicating parties.
8. What is the difference between a session key and a master key?
9. What are the roles of the public and private key?
10. What requirements must a public key cryptosystem fulfill to be a secure algorithm?
|
Adjusted gross income
: We covered a wide variety of deductions both FOR and FROM Adjusted Gross Income (AGI).
|
|
Conduct a great example of a simplified job analysis
: Conduct a great example of a simplified job analysis
|
|
What procedure does organization use to account for fifo
: In the summary of significant accounting policies, what procedure does your organization use to account for inventory (FIFO, LIFO, etc)?
|
|
Outline the important sub-issues evident in case
: In 1993, Emily Levine graduated at the top of her class at the University of Southern California, completing a degree in political science, majoring in internat
|
|
Briefly define categories of security services
: What is the difference between link and end-to-end encryption and List ways in which secret keys can be distributed to two communicating parties
|
|
Does organization report an allowance for uncollectible
: Does your organization report an allowance for uncollectible accounts in the balance sheet? If so, how much is reported for the most recent year?
|
|
How effective was the teamwork
: Consider a job you currently have or held. To what extent did you work in teams, what was the project or initiative, and how effective was the teamwork?
|
|
Calculate the acid-test ratio for the past two years
: Review the balance sheet and other important financial statements. Based on this information, how would you rate the bankruptcy risk of your company?
|
|
Briefly discuss the employment boarding
: Briefly discuss the employment boarding , it importance and value if implemented effectively?
|