Reference no: EM13111824
Identifying Potential Malicious Attacks, Threats and Vulnerabilities
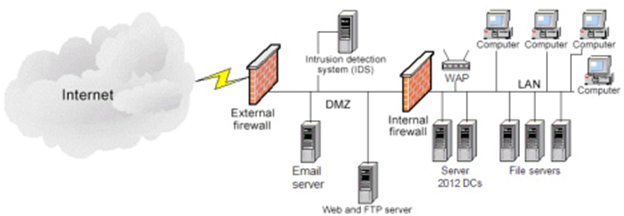
You have just been hired as an Information Security Engineer for a videogame development company. The organization network structure is identified in the below network diagram and specifically contains:
1) 2 - Firewalls
2) 1 - Web / FTP server
3) 1 - Microsoft Exchange Email server
4) 1 - Network Intrusion Detection System (NIDS)
5) 2 - Windows Server 2012 Active Directory Domain Controllers (DC)
6) 3 - File servers
7) 1 - Wireless access point (WAP)
8) 100 - Desktop / Laptop computers
9) VoIP telephone system
The CIO has seen reports of malicious activity being on the rise and has become extremely concerned with the protection of the intellectual property and highly sensitive data maintained by your organization. As one of your first tasks with the organization, the CIO requested you identify and draft a report identifying potential malicious attacks, threats, and vulnerabilities specific to your organization. Further, the CIO would like you to briefly explain each item and the potential impact it could have on the organization.
Write a four to five (4-5) page paper in which you:
1. Analyze three (3) specific potential malicious attacks and / or threats that could be carried out against the network and organization.
2. Explain in detail the potential impact of the three (3) selected malicious attacks.
3. Propose the security controls that you would consider implementing in order to protect against the selected potential malicious attacks.
4. Analyze three (3) potential concerns for data loss and data theft that may exist in the documented network.
5. Explicate the potential impact of the three (3) selected concerns for data loss and data theft.
6. Propose the security controls that you would consider implementing in order to protect against the selected concerns for data loss and data theft.
|
List the four large molecules of life
: Before bringing a new drug to the marketplace, extensive testing is done on the drug by administering the drug to large numbers of individuals. Explain the importance of the scientific method, sample size, controls and variable in the drug evaluat..
|
|
Discussion on global warming contributors
: Some people think that driving a car, cooking on an outdoor grill, and using electricity produced by coal-fired generators contribute to global warming. What is the reasoning behind their thinking?
|
|
P-values-hypothesis testing and two sample groups
: In a sample of 210 men, 35 prefer sugar free soft drinks. In a sample of 220 women, 42 prefer sugar free soft drinks. Using a significance level of 0.05, test whether women prefer sugar free drinks more than men. Calculate the p-value.
|
|
What enzyme pathway of arachidonic acid is interrupted
: What enzyme pathway of arachidonic acid is interrupted/broken by aspirin and ibuprofen?
|
|
Analyze specific potential malicious attacks
: Analyze specific potential malicious attacks and / or threats that could be carried out against the network and organization and explain in detail the potential impact of the three selected malicious attacks
|
|
What would the response be from an off ganglion cell
: You go from a lit room to a dark room. What would the response be from an OFF ganglion cell? Why so?
|
|
Formulating null and alternative hypotheses
: Formulate the null and alternative hypotheses for a hypothesis test. Identify the population and describe how to select a random sample for a hypothesis test. State in clear terms the conclusion that should be given if the null hypothesis is rejec..
|
|
Information about formulating null and alternative hypothese
: Formulate the null and alternative hypotheses for a hypothesis test. Identify the population and describe how to select a random sample for a hypothesis test. State in clear terms the conclusion that should be given if the null hypothesis is rejec..
|
|
Explain the major advantage of increasing compression ratio
: The compression ratio of today's cars is so much higher than in cars of years past. What is the major advantage of increasing the compression ratio?
|