Packet Structure
|
Version
Number
(4 bits)
|
Header
Length
(4 bits)
|
Type of
Service (8
bits)
|
Total Length (16 bits)
|
|
ID (16 bits)
|
Flags
(3bits)
|
Flag Offset (13 bits)
|
|
Time To Live
(8 bits)
|
Protocol (8
bits)
|
Header Checksum (16 bits)
|
|
Source (32 bits)
|
|
Destination (32 bits)
|
|
Options
|
Version Number : The current version is Version 4 (0100).
1. Header Length: We could have multiple sized headers so we need this field. Header will always be a multiple of four bytes and so we can have a maximum length of the field as fifteen, so the maximum size of the header is sixty bytes ( twenty bytes are mandatory ).
2. Type Of Service (ToS) : This helps the router in taking the correct routing decisions.
The structure is:
First three bits: They identify the precedences that is the priority of the packets.
Next three bits :
o D bit - D stands for delay. If the D bit is set to one, then this means that the application is delay aware, so we must try to route the packet with minimum delay.
o T bit - T stands for throughput. This shows us that this particular operation is throughput sensitive.
o R bit - R stands for reliability. This tells us that we must route this packet through a more reliable network.
Last 2 bits: The last 2 bits are never used. unluckily, no router in this world looks at these bits and so no application sets them these days. The 2nd word is meant for managing fragmentations. If a link cannot transmit big packets, then we fragment the packet and put sufficient information in the header for recollection at the destination end.
ID Field: The source and ID field together will symbolize the fragments of a unique packet. So every fragment will have a different ID.
Offset : It is a thirteen bit field that represents where in the packet, the current fragment starts. every bit represents eight bytes of the packet. So the packet size can be at most sixty four kB. each fragment except the last one have to its size in bytes as a multiple of eight in order to ensure compliance with this structure. The basis why the position of a fragment is given as an offset value in its place of simply numbering each packet is since refragmentation may occur anywhere on the path to the other node. Fragmentation, although supported by IPv4 is not encouraged. The reason is if even one fragment is gone the entire packet needs to be unnecessary. A quantity M.T.U (Maximum Transmission Unit) is definite for each connection in the route. It is the size of the biggest packet that can be handled by the connection. The Path-M.T.U is then defined as the size of the biggest packet that can be handled by the path. It is the smallest amount of all the MTUs along the path. Given information about the path MTU we can send packets with sizes lesser than the path MTU and thus prevent fragmentation. This will not totally prevent it because routing tables may change leading to a change in the path.
Flags :It has 3 bits -
o M bit : If M is 1, then there are more fragments on the way and if M is zero, then it is the final fragment
o DF bit : If this bit is sent to one, then we should not fragment such a packet.
o Reserved bit : This bit is not used.
Reassembly can be done only at the destination end and not at any intermediate node. This is because we are taking into account Datagram Service and so it is not surefire that all the fragments of the packet will be sent thorough the node at which we desire to do reassembly.
Total Length : It includes the IP header and all that comes after it.
Time To Live (TTL) : By this field, we could set the time inside which the packet should be delivered or else smashed. It is firmly treated as the number of hops. The packet supposed to reach the destination end in this number of hops. Each router decreases the value as the packet goes through it and if this value becomes 0 at a particular router, it can be shattered.
Protocol : This specifies the module to which we supposed to hand over the packet (UDP or TCP ). It is the next encapsulated protocol.
Value Protocol
0 Pv6 Hop-by-Hop Option.
1 ICMP( Internet Control Message Protocol).
2 IGMP(Internet Group Management Protocol)and RGMP, Router- port Group Management Protocol.
3 GGP, Gateway to Gateway Protocol.
4 IP in IP encapsulation.
5 ST, Internet Stream Protocol.
6 TCP, Transmission Control Protocol.
7 UCL, CBT.
8 EGP, Exterior Gateway Protocol.
9 IGRP.
10 BBN RCC Monitoring
11 NVP, Network Voice Protocol.
12 PUP.
13 ARGUS.
14 EMCON, Emission Control Protocol.
15 XNET, Cross Net Debugger.
16 Chaos.
17 UDP, User Datagram Protocol.
18 TMux( Transport Multiplexing Protocol).
19 DCN Measurement Subsystems.
-
-
255
3. Header Checksum : This is the usual checksum field used to discover errors. Since the TTL field is altering at every router so the header checksum ( upto the options field ) is checked and recalculated at every router.
4. Source : It is the IP address of the source node
5. Destination : It is the IP address of the destination node.
6. IP Options : The options field was created in order to allow features to be added into IP as time passes and requirements change. Currently five options are specified although not all routers hold them and They are:
o Securtiy: It tells us how secret the information is. In theory a military router can use this field to specify not to route through particulars routers. In practice no routers support this field.
o Source Routing: It is used when we wish for the source to dictate how the packet traverses the network. It is of two types
-> Loose Source Record Routing (LSRR): It requires that the packet traverse a list of specified routers and in the order specific but the packet may pass though some other routers as well.
-> Strict Source Record Routing (SSRR): It requires that the packet traverse only the set of specified routers and nothing else. If it is not achievable, the packet may dropped with an error message sent to the host.
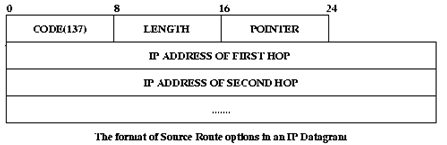
The above is the format for SSRR. For LSRR the code is 131.
o Record Routing :

In this the intermediate routers put there IP addresses in the header, so that the destination end knows the entire path of the packet room for storing the IP address is specified by the source itself. The pointer field points to the spot where the next IP address has to be written. Length field shows the number of bytes kept by the source for writing the IP addresses. If the room provided for storing the IP addresses of the routers visited, falls short whereas storing these addresses, then the following routers do not write their IP addresses.
o Time Stamp Routing :
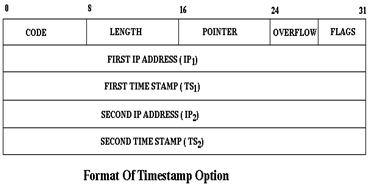
It is parallel to record route option except that nodes also attach their timestamps to the message. The latest fields in this option are
-> Flags: It can have the these values
§ 0- Enter only timestamp.
§ 1- The nodes ought to enter Timestamp as well as their IP.
§ 3 - The source specifies the IPs that should enter their timestamp. A particular point of interest is that only if the IP is the same as that at the pointer then the time is inserted. therefore if the source specifies IP1 and IP2 but IP2 is 1st in the path then the field IP2 is left unfilled, even after having reached IP2 but before reaching IP1.
-> Overflow: It stores the no. of nodes that were not capable to add their timestamps to the packet. The maximum value is fifteen.
o Format of the type/code field
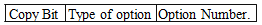
§ Copy bit: It says whether the option is to be copied to every fragment or not. a value of 1 stands for copying and zero stands for not copying.
§ Type: It is a two bit field. Currently specified values are zero and two. zero means the option is a control option while two means the option is for measurement
§ Option Number: It is a five bit field which specifies the option number.
For all options a length field is put in order that a router not recognizable with the option will know how many bytes to skip. Thus every option is of the form
o TLV: Type/Length/Value. This format is followed in not only in IP but in nearly all main protocols.
Email based Computer Science assignment help - homework help at Expertsmind
Are you searching Computer Science expert for help with Packet Structure questions? Packet Structure topic is not easier to learn without external help? We at www.expertsmind.com offer finest service of Computer Science assignment help and computer science homework help. Live tutors are available for 24x7 hours helping students in their Packet Structure related problems. We provide step by step Packet Structure question's answers with 100% plagiarism free content. We prepare quality content and notes for Packet Structure topic under computer science theory and study material. These are avail for subscribed users and they can get advantages anytime.
Why Expertsmind for assignment help
- Higher degree holder and experienced experts network
- Punctuality and responsibility of work
- Quality solution with 100% plagiarism free answers
- Time on Delivery
- Privacy of information and details
- Excellence in solving computer science questions in excels and word format.
- Best tutoring assistance 24x7 hours