Needham-Schroeder Authentication Protocol
This is similar to a bug-fix to the KDC scheme to get rid of replay attacks. A three-way handshake (using nonce numbers) very like to the ubiquitous TCP three-way handshake is used among communicating parties. When A sends a arbitrary number RA to KDC. KDC send back a ticket to A which have the common key to be used.
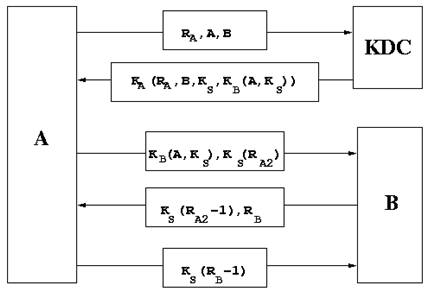
RA, RB and RA2 are nonce numbers. RA is used by A to converse with the KDC. On getting the appropriate reply from the KDC ,A will starts communicating with B, whence another nonce number RA2 is used. The first 3 messages tell B that the message has come from KDC and it has authenticated A. The 2 last message authenticates B. The repond from B contains RB, which is a temporary number generated by B. The last message authenticates A. The last 2 messages also remove the possibility of replay attack.
However, the problem with this scheme is that if somehow an intruder gets to know the key KS ( maybe a year later ), then he can replay the entire thing ( provided he had stored the packets ). One possible solution can be that the ticket contains a time stamp. We can also put a condition that A and B should change the key every month or so. To improve the protocol, B should also involve KDC for authentication. We look at one likely improvement here. which is a diverse protocol.
Email based Computer Science assignment help - homework help at Expertsmind
Are you searching Computer Science expert for help with Needham-Schroeder Authentication Protocol questions? Needham-Schroeder Authentication Protocol topic is not easier to learn without external help? We at www.expertsmind.com offer finest service of Computer Science assignment help and computer science homework help. Live tutors are available for 24x7 hours helping students in their Needham-Schroeder Authentication Protocol related problems. We provide step by step Needham-Schroeder Authentication Protocol question's answers with 100% plagiarism free content. We prepare quality content and notes for Needham-Schroeder Authentication Protocol topic under computer science theory and study material. These are avail for subscribed users and they can get advantages anytime.
Why Expertsmind for assignment help
- Higher degree holder and experienced experts network
- Punctuality and responsibility of work
- Quality solution with 100% plagiarism free answers
- Time on Delivery
- Privacy of information and details
- Excellence in solving computer science questions in excels and word format.
- Best tutoring assistance 24x7 hours